Security is no longer a secondary consideration in today’s rapidly evolving software development environment. Development models of the past tended to isolate security as a distinct stage, which would introduce vulnerabilities not found until the later stages of the lifecycle. This resulted in expensive patches, delays, and even security compromise. DevSecOps process, a mix of Development, Security, and Operations, is a bid to incorporate security into each phase of the software development lifecycle (SDLC). It’s a refinement of DevOps that embeds security practices in development and not as an afterthought.
This article will explore the DevSecOps process in detail, including its importance, best practices, implementation strategies, and challenges. By the end, you’ll have a clear understanding of how to integrate security into your DevOps pipeline to build more resilient applications.
What is DevSecOps?
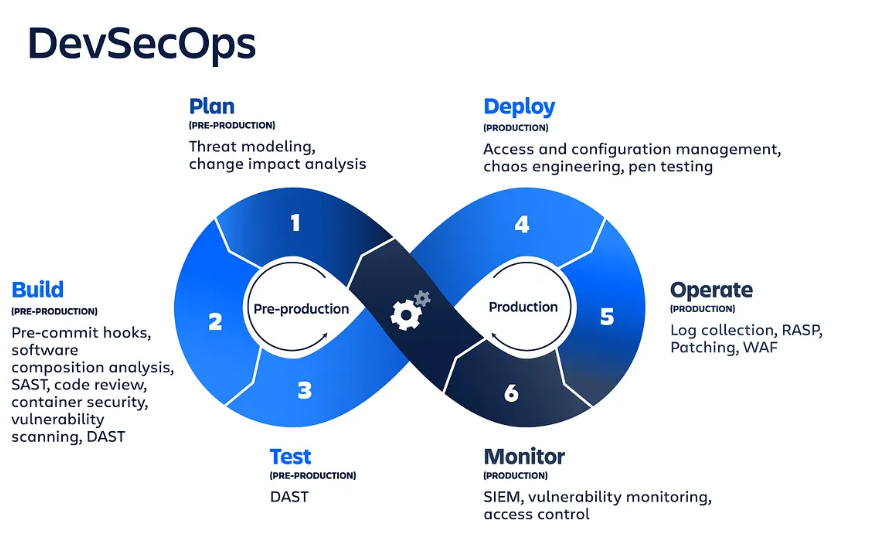
DevSecOps is a practice that involves ensuring security is embedded in each phase of software development. Rather than considering security as an isolated phase, it includes security testing, compliance validation, and risk assessment in the CI/CD (Continuous Integration/Continuous Deployment) pipeline.
The primary objective of DevSecOps is “security as code”, where security is automated, continuous, and a natural part of the development process.
Why is DevSecOps Important?
- Shifts security left – Security is implemented early on in the development process instead of at the last minute.
- Lessens vulnerabilities – Ongoing security testing identifies and addresses threats ahead of deployment.
- Increases compliance – Assists with regulatory compliance like GDPR, HIPAA, and ISO 27001.
- Ensures better quality software – Secure coding and automation testing result in more secure apps.
- Accelerates delivery – Automation of security takes away time consumed in patching vulnerabilities later.
The DevSecOps Process
There are a number of essential phases involved in the DevSecOps process that concentrate on incorporating security into development and operations. The following is an overview of the most important steps.
1. Planning and Security Design
Security is incorporated into planning in the initial phase of the DevSecOps process pipeline. In this step, there is:
Get exclusive access to all things tech-savvy, and be the first to receive
the latest updates directly in your inbox.
- Threat Modeling: Determining possible security vulnerabilities and attack paths.
- Defining Security Requirements: Establishing security policies, compliance standards, and best practices.
- Choosing Security Tools: Selection of automated security testing tools, code analysis, and vulnerability scanners.
- Access Controls & Identity Management: Enforcement of role-based access controls (RBAC) and multi-factor authentication (MFA).
Best Practice: Engage the security teams right from the initial stages of the development lifecycle so that security requirements are baked into architecture and design decisions.
2. Secure Coding & Development
Security best practices must be imposed during development. This includes:
- Secure Coding Standards: Implementing OWASP Top 10 and Secure Software Development Framework (SSDF).
- Automated Static Code Analysis (SAST): Scanning source code for security vulnerabilities prior to merging.
- Dependency Management: Scanning third-party libraries for vulnerabilities using tools such as Snyk or Dependabot.
- Secrets Management: Storing sensitive information (API keys, passwords) encrypted and secured.
Best Practice: Train developers in secure coding practices and provide frequent security training.
3. Continuous Integration (CI) with Security Checks
Including security in the CI process guarantees early detection of vulnerabilities. This involves:
- Automated Security Testing: Executing security scans in parallel with unit and integration tests.
- Dynamic Application Security Testing (DAST): Testing executed applications for vulnerabilities.
- Interactive Application Security Testing (IAST): Merging static and dynamic testing for in-depth analysis.
- Configuration Management: Guaranteeing security settings are enforced through tools such as Ansible or Terraform.
Best Practice: Build security tools into CI pipelines to automatically identify and correct security problems.
4. Continuous Delivery (CD) and Security Automation
Security automation ensures integrity of code as it advances towards production.
- Container Security: Vulnerability scanning of container images prior to deployment.
- Infrastructure as Code (IaC) Security: Secure IaC scripts (Terraform, CloudFormation).
- Secrets Management: Storing sensitive credentials securely using tools like HashiCorp Vault.
- Policy Enforcement: Applying automated compliance checks to achieve security standards.
Best Practice: Automate security testing throughout each phase of the CD pipeline to avoid security gaps.
5. Continuous Monitoring & Incident Response
After the app is deployed, continuous security monitoring is important to catch and mitigate threats.
- Security Information and Event Management (SIEM): Collecting and processing security logs.
- Threat Detection: Employing AI-driven tools to detect abnormal behavior.
- Incident Response Plan: Maintaining a clearly defined response plan in the event of security breaches.
- Penetration Testing: Performing regular ethical hacking drills to determine vulnerabilities.
Best Practice: Utilize real-time monitoring tools such as Splunk, ELK Stack, or AWS Security Hub to actively detect threats.
DevSecOps Best Practices
To be able to implement DevSecOps process successfully, organizations must adhere to these best practices:

- Adopt a Security-First Culture: Security must be made a team-wide responsibility.
- Automate Security Processes: Utilize security automation tools to minimize manual effort.
- Enforce Least Privilege: Limit access according to the principle of least privilege.
- Regular Security Training: Train teams on secure coding and security best practices.
- Use Multi-Layered Security: Implement multiple security controls, including firewalls, encryption, and access controls.
- Integrate Security into CI/CD: Make security testing occur at each development stage.
- Conduct Regular Audits: Regularly evaluate security posture and compliance.
Challenges in DevSecOps Implementation
Although DevSecOps is provided with several advantages, there are challenges involved as well:
- Resistance to Change: Teams will be resistant to adjusting to security-first development.
- Tool Overload: It is difficult to manage various security tools.
- Skill Gaps: All developers aren’t equipped with security best practices training.
- False Positives: Security scanners might detect harmless code as vulnerabilities.
- Balancing Security & Speed: Attaining security with fast release cycles.
Solution: Organizations need to invest in security training, normalize security tools, and transition into security by integrating security into current workflows over time.
DevSecOps Toolchain
Organizations require the appropriate set of tools to successfully adopt DevSecOps. The following are some widely used security tools:
| Category | Tool Examples |
|---|---|
| Static Code Analysis (SAST) | SonarQube, Checkmarx |
| Dynamic Security Testing (DAST) | OWASP ZAP, Burp Suite |
| Container Security | Trivy, Aqua Security |
| Secrets Management | HashiCorp Vault, AWS Secrets Manager |
| Infrastructure as Code (IaC) Security | Terraform Security, KICS |
| CI/CD Security | GitHub Actions Security, GitLab Security Scanning |
| Monitoring & SIEM | Splunk, ELK Stack, AWS Security Hub |
Best Practice: Choose a set of these tools to automate security along the pipeline.
Conclusion
DevSecOps is a revolutionary method that merges security into each phase of the software development cycle. By moving security left, automating testing, and imposing best practice, organizations can create secure applications without compromising on speed.
Despite challenges, these are surmountable with the right training, tool choice, and cultural shift toward security-first development. With DevSecOps process, security isn’t a bottleneck but rather an enabler of innovation and dependability.
By adopting DevSecOps, organizations can enhance software security, compliance, and resilience ensuring applications stay safeguarded against contemporary cyber threats.
FAQs
What is DevSecOps?
DevSecOps is an abbreviation for Development, Security, and Operations. DevSecOps process embeds security practices into the entire software development life cycle (SDLC) instead of appending security as an afterthought. This way, security is made continuous, automated, and collaborative.
How is DevSecOps Different from DevOps?
DevOps aims to enhance the collaboration between development and operations to release software in a quicker manner. DevSecOps introduces security to the combination, so software is not just quick but also secure. DevSecOps process, in essence, moves security “left” to the initial development phases.
What Is the Role of Automation in DevSecOps?
Automation is needed in DevSecOps process as it can provide continuous security without bogging down the pipeline. Automated tools for testing can conduct code analysis, vulnerability scanning, and compliance testing at all phases of development.



