Call centers are under pressure. Attackers see them as easy targets, regulators treat them as compliance hotspots, and customers expect fast, frictionless service. That’s a hard balance to strike.
On one side, you’ve got to lock down sensitive data, meet industry regulations, and protect against fraud attempts that arrive by phone, email, or chat. On the other hand, you can’t let those safeguards slow down conversations or frustrate customers. After all, security that adds friction doesn’t last long in a real-world support environment.
Most call centers don’t fail because they lack tools; they fail because they deploy the wrong ones or overcomplicate their stack.
This article cuts through the noise and focuses on the technologies, practices, and cultural shifts that actually help call centers stay secure without grinding operations to a halt.
The real threats facing today’s call centers
Call centers are prime targets for modern cyberattacks. Phishing, social engineering, and VoIP fraud are now everyday concerns. The 2024 Verizon Data Breach Investigations Report shows that over two-thirds (68%) of breaches involve a non-malicious human element, meaning mistakes or falling for social engineering traps
For call centers, the human factor overlaps with the risks of voice and VoIP systems. Attackers use spoofed caller IDs, impersonate customers, and exploit inattentive agents. Traditional security measures often focus on technology, but these tactics require context-aware defenses.
Get exclusive access to all things tech-savvy, and be the first to receive
the latest updates directly in your inbox.
One way to strengthen protection is to integrate an IP geolocation API into call center workflows. Tools like IPinfo’s geolocation services can flag suspicious activity such as a login attempt from a high-risk region or an IP that doesn’t match expected agent behavior. When combined with fraud detection systems, this extra layer helps call centers spot anomalies early and turn raw network data into actionable security intelligence.
5 Security technologies every call center actually needs
With so many products marketed as “essential,” it helps to focus on what makes a real difference right now.
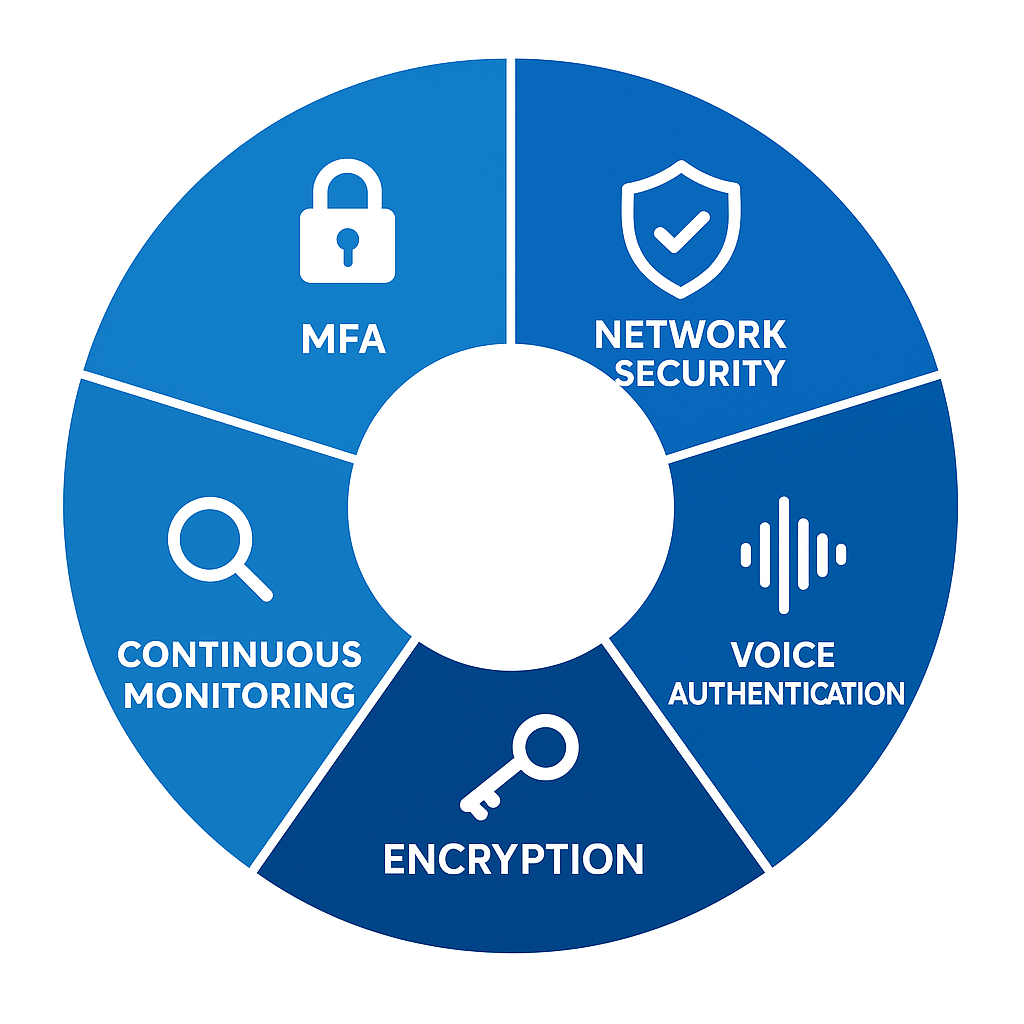
1) Smarter Authentication Beyond Passwords
Passwords alone don’t cut it. Multi-factor authentication (MFA), behavioral biometrics, and voice verification create stronger barriers. MFA combines a PIN, a device, and a personal identifier like a voice pattern.
Behavioral biometrics add another layer by recognizing patterns in how someone types or navigates software. These measures make it much harder for attackers to impersonate legitimate users while keeping the process manageable for customers and agents.
2) Network-Level Security for VoIP
VoIP networks are flexible but also vulnerable to session hijacking and endpoint attacks, especially when agents work remotely. Protection typically involves intrusion prevention, network segmentation, and secure tunneling for off-site staff.
Cloud-native platforms simplify this. Aircall, for example, functions as a customer service AI tool with security built directly into its phone system, reducing the need for teams to manually configure VPNs or maintain legacy PBX hardware. That foundation makes it easier for teams to extend workflows into CRMs or help desks without opening up new vulnerabilities.
3) Voice Authentication Systems
Voice authentication analyzes speech characteristics such as pitch and cadence to confirm identity. It avoids the pitfalls of security questions that can often be guessed or researched online.
When well implemented, these systems verify callers in the background without slowing down conversations. That balance is important: strong enough to deter fraud but subtle enough that customers barely notice it’s happening.
4) End-to-End Data Encryption
Calls, recordings, chat logs, and stored customer information all need encryption. Protecting data in motion and at rest ensures that even if it’s intercepted, it remains inaccessible without the proper keys.
Good encryption systems also support role-based access, so only the right people can view sensitive recordings. Pairing encryption with strong key management creates a safer environment across the entire data lifecycle.

5) Continuous Monitoring and Threat Analytics
Call center security can’t rely on periodic checks. Threats appear in real time, whether it’s suspicious login attempts, sudden spikes in call activity, or agents accessing records outside their normal queues. Continuous monitoring gives teams the visibility to identify these issues quickly and respond before they escalate.
Modern monitoring platforms use machine learning to understand what “normal” looks like and flag deviations. A sudden surge of international calls from a single account or repeated login attempts from unexpected locations could indicate compromise.
Is the cloud safer for call centers?
A move to the cloud can expose call centers to risks if not managed carefully. Misconfigured permissions, downtime, or data loss during transfer are all common pitfalls. The best way to minimize disruption is to approach migration in phases and follow cloud security best practices:
- Run a structured risk assessment: Map where customer data currently resides, who has access to it, and which compliance frameworks apply.
- Use hybrid strategies when possible: Keep sensitive workloads on-premises while moving less-critical processes to the cloud.
- Plan for disaster recovery: Strong backup and failover systems ensure that if an outage or breach occurs, operations can continue without major service disruption.
Built-in security perks of cloud contact centers
Well-designed cloud platforms provide advantages that traditional systems struggle to match:
- Automatic patching reduces the window of exposure to new vulnerabilities.
- Centralized monitoring improves visibility and helps detect unusual patterns across distributed teams.
- Universal updates lower the risk of lagging behind on security versions.
- Managed integrations (e.g., CRMs and help desks via APIs) apply safeguards by default, minimizing the risk of misconfigured connections.
- Built-in protections level the playing field for smaller or fast-growing teams that lack large security departments.
Who owns your data in the cloud?
Cloud providers may host and process your data, but responsibility doesn’t shift entirely to them. Under the GDPR, organizations usually act as the data controller, while providers are the processor handling information on their behalf.
To stay compliant, call centers should:
- Define roles up front through contracts and processing agreements.
- Clarify deletion and audit policies in service terms.
- Address data sovereignty if records cross borders.
- Keeping these points explicit avoids confusion and reduces legal risk during or after migration.
Using AI and analytics to stay ahead of threats
AI is quickly becoming a cornerstone of call center security, not just for detection but for prevention.
- Anomaly detection learns what “normal” looks like (such as typical call volumes or login behavior) and flags deviations that might signal account compromise or fraudulent activity. This makes it possible to spot problems earlier than rule-based systems that only trigger after a known signature.
- Natural language processing (NLP) can analyze conversations in real time to identify social engineering attempts. For example, if a caller repeatedly presses for sensitive data using unusual phrasing, the system can alert an agent or supervisor without disrupting the interaction.
- Predictive analytics takes it one step further by assessing which accounts or processes are most likely to be targeted, enabling teams to add safeguards before an incident occurs.
AI-driven dashboards prioritize the most urgent risks, highlight clear next steps, and cut down on noise from false positives. Instead of drowning in alerts, security teams and supervisors get focused recommendations that help them act quickly and keep operations running smoothly.
Stopping insider threats before they happen
While external attacks draw attention, insider threats remain significant, whether from carelessness or intent.
Why access control matters more than you think
Least-privilege access limits what each agent can see. As roles shift, dynamic permissions ensure access matches responsibilities. Separation of duties further prevents any single person from controlling too much data.
Restricting access not only lowers risk but also simplifies audits. Regulators can clearly see who had access to what information, and when.
Spotting risky behavior without over-surveilling
Employees shouldn’t feel constantly watched, but ignoring risky activity isn’t an option. Behavior analytics offer a middle ground by detecting patterns that stand out, like odd login hours or attempts to access unrelated records.
By focusing on anomalies rather than blanket monitoring, managers can protect systems while maintaining employee trust.
Training agents to be security assets
Agents play a direct role in keeping call centers secure. Regular training helps them recognize phishing attempts, protect sensitive data, and respond effectively when something looks suspicious.
Simulations, like fake phishing emails, reveal gaps and provide opportunities to improve. Progress can be measured to show that training is paying off. When agents see themselves as part of the defense, overall security strengthens.
Compliance without the overhead
Security and compliance often overlap. Ignoring compliance can be costly, but treating it as a box-checking exercise creates unnecessary burdens.
- Automating compliance checks in real time — Automation reduces manual effort by redacting sensitive data like credit card numbers from recordings to meet PCI DSS requirements. Continuous monitoring keeps teams aligned day to day, so audits don’t become last-minute fire drills.
- Security audits that don’t slow you down — Smaller, more frequent audits and penetration tests catch issues earlier without disrupting daily operations. This approach maintains a strong security posture while keeping agents focused on serving customers.
- Incident response basics — Clear playbooks outline responsibilities, containment steps, and notification protocols. Predefined communication templates ensure consistent updates for regulators and customers, building trust even during disruptions.
The Bottom Line on Securing Your Call Center
Securing a call center is all about combining practical technologies with disciplined processes. Cloud platforms bring built-in protections but require careful oversight.
AI can spot anomalies, but only if paired with clear escalation workflows. Encryption protects data, but only if keys are managed correctly.
Just as important is culture. Agents trained as security partners, not liabilities, often become the strongest defense. Compliance, too, should be woven into daily workflows, not treated as a bureaucratic burden.


