SPF, DKIM, DMARC are more than just technical email configurations. They have a detrimental impact on email delivery. They work together to ensure better email delivery.
In a nutshell, all three approaches are used by Internet Service Providers (ISPs) to verify email authenticity. Is the sender truly who they claim to be?
You must demonstrate that you are a valid sender in order to pass via ISP filters. How can you show you’re not sending on someone else’s behalf and that your identity hasn’t been stolen? By making use of SPF DKIM DMARC.
Text records that expressly prove and safeguard a sender’s authenticity are known as SPF DKIM DMARC records.
You can set up all of these records on CyberPanel using: Achieve 10/10 Email score with CyberPanel!
SPF Records
The Sender Policy Framework, or SPF for short, is an email validation protocol for detecting and blocking email counterfeiting. It enables mail intermediaries to verify that incoming mail from a certain domain originates from an IP address that has been permitted by the domain’s administration. An SPF record is a TXT record in the DNS (Domain Name System) that indicates which IP addresses and/or servers are permitted to send mail “from” that domain. It’s similar to having a trustworthy and identifiable return address on a postcard: most individuals are considerably more likely to open a letter if the return address is reliable and recognizable.
Get exclusive access to all things tech-savvy, and be the first to receive
the latest updates directly in your inbox.
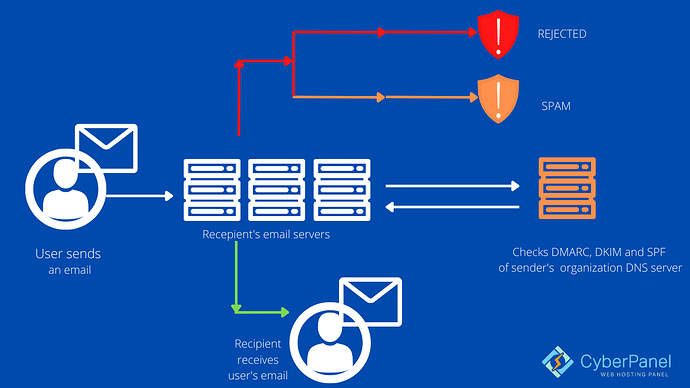
ISPs examine the message’s Return-Path domain after it has been transmitted. The IP address that sent the email is then compared to the IP address stated in the Return-Path domain’s SPF record to verify if they match. If so, the ISPs verify the SPF verification and send the message.
Example of an SPF record:
v=spf1 ip4:168.119.13.219 include:mailgun.org include:zoho.com include:mxlogin.com ~all
Why is it important?
SPF is a “proposed standard” that aids in the protection of email users from spammers. Forged “from” addresses and domains are frequently used in email spam and phishing. As a result, most people consider publishing and checking SPF records to be one of the most effective and straightforward anti-spam strategies. If you have a good sending image, a spammer may try to send email from your domain in order to benefit from your ISP’s good sender reputation. However, correctly configured SPF authentication informs the recipient ISP that, while the domain may be yours, the transmitting server is not allowed to send mail on your behalf.
Even if a subdomain does not have its own SPF record, an SPF record in the top domain will automatically authenticate it.
Advantages
When spammers gain control of your domain, they will attempt to send unwanted emails. This will hurt your credibility as well as your capacity to deliver. If you haven’t yet authenticated your domain, you should make it a priority. SPF ensures that your deliverability is high in the following ways:
• Notifies receivers of third-party offers.
If spammers employ a relay, an SPF record ensures that the end-user is notified.
• Quick access to inboxes
Because of the implementation of SPF, email recipients will gain trust in your brand and your future emails will have secure access to their inboxes.
• Required for some recipients
Some email recipients just want an SPF record and will designate emails as spam if they don’t have one. Otherwise, it’s possible that your email will bounce.
• Improves the sender’s score
Every outgoing mail server’s Sender Score is calculated using traditional email metrics such as unsubscribes and spam files. SPF improves your Sender Score, which improves email delivery.

Disadvantages
The SPF system has a couple of limitations. The following are the details:
• Doesn’t function on emails that have been forwarded
Because forwarded emails do not contain the original sender’s identification and appear to be spam messages, they frequently fail the sender policy framework test.
• Isn’t updated on a regular basis
Many domain managers may not be able to keep their SPF records up to date on a regular basis.
• Despite the fact that the server has changed, you must update.
When using a third-party email provider, the domain must update the SPF record every time the service provider’s servers change, which adds to the workload.
How does it work?
Receiving servers check for SPF by looking up the domain’s Return-Path value in the email’s headers. This return path is used by the recipient server to look for a TXT record in the sender’s DNS server. If SPF is enabled, it will display a list of all approved servers from which mail can be sent. The SPF check will fail if the IP address is not in the list.
SPF records are divided into two sections: qualifiers and mechanisms.
- It is possible to define who is allowed to deliver mail on behalf of a domain using mechanisms. One of four qualifiers can be used if those conditions are met.
- When a mechanism is matched, qualifiers are the actions that are taken. The default + is used if no qualifier is specified. The four types of qualifiers that can be used to configure SPF email policies are listed below.
DKIM Records
DKIM (DomainKeys Identified Mail) allows an organization (or message handler) to bear the responsibility for a message while it is in transit. DKIM adds a new domain name identifier to a message and utilizes cryptographic techniques to verify its authorization. Any other identifier in the message, such as the author’s From: field, has no effect on the identification. DKIM, a TXT record signature, also helps to establish confidence between sender and receiver.
Why is it important?
While DKIM isn’t essential, it makes your emails appear more authentic to your recipients and makes them less likely to end up in the Junk or Spam folders. Spoofing email from trustworthy domains is a common tactic for dangerous spamming campaigns, and DKIM makes it more difficult to spoof email from DKIM-enabled domains.
DKIM is compatible with current email architecture and works in conjunction with SPF and DMARC to provide additional layers of security for email senders. Even if their mail servers don’t support DKIM signatures, they can still receive signed messages. It’s a security mechanism that’s optional, and DKIM isn’t a widely used standard.
Advantages
Signing and verifying are two independent actions provided by DKIM. Either of them can be handled by a mail transfer agent module (MTA). Private and Public DKIM keys are created in pairs.
DKIM uses “asymmetric cryptography,” which is also known as “public-key cryptography.” DKIM employs a “private key” to establish a signature after a message is received and before it is transmitted to its intended recipient. The message has this signature attached to it. When the message is sent to its intended recipient, the destination server requests the sender’s public key in order to validate the signature. The destination server can assume the sender is who they claim to be if the public key permits it to decrypt the given signature to the same value it computes as the signature.
Disadvantages
- SPF record type – The SPF record can only be published in TXT format. The “SPF” type record is no longer supported and should be avoided.
- Several records – Adding multiple SPF records to a domain. Extra records must be deleted or merged with the current one.
- Using the include technique to refer to a non-existing record is referred to as including a non-existing record. Included items that aren’t valid must be eliminated.
- When in doubt, use -all. While using it without completely including all possible sources increases the risk of real emails being rejected.
- Too many records – Including too many records, particularly in the _spf.google.com and spf.protection.outlook.com zones, may result in an excessive number of lookups. These records need to be optimized.
How does it work?
DKIM generates a public and private key pair via asymmetric encryption. In the DNS of the sender domain, the public key is published as a specific TXT record. The private key is used to make each email’s signature unique.
A privacy algorithm assigned a random signature as part of the email’s headers using your private key and the contents of the email.
When an outbound mail server sends a message, it generates and attaches a unique DKIM signature header to the message. Two cryptographic hashes, one of defined headers, and one of at least some part of the message content are included in this header. The DKIM header also includes details on how the signature was created.
When an SMTP server gets an email with such a signature in the header, it queries the DNS for the public key TXT record for the sending domain. The receiving server will be able to verify whether the email was sent from that domain and was not tampered with in transit using the public key.
The recipient email service provider may classify the email as spam or ban the sender’s IP address entirely if the check fails or the signature does not exist. This makes it more difficult for scammers to impersonate your domain address in emails.
DMARC Records
Domain-based Message Authentication Reporting and Conformance (DMARC) is a free and open technical specification. In a DMARC implementation, the core is a DMARC record that defines the rulesets. If a domain is DMARC-enabled, this record informs email recipients. This means the domain owner can specify which policy he/she wants to use in the DMARC record of the domain. DNS (Domain Name Service) records are in essence DMARC records. A DMARC DNS record can be implemented to use DMARC. Users of email receivers that have adopted DMARC will be able to use this record. As a result, your DMARC policy will allow you to keep track of every message sent to your domain.
Therefore, the organization that publishes the DMARC record will be able to specify how non-compliance will be handled. It is possible to monitor (and deliver) messages, move them to junk folders, or reject them.
Why is it important?
Any email that does not match is considered fraudulent and will be ignored. Phishing is the deceptive activity of sending malicious emails posing as someone else in order to obtain a user’s credit card or other personal information. As a result, by using DMARC, you are safeguarding yourself.
A successful DMARC installation would gradually ramp up from various levels of quarantine to full rejection. A good practice also necessitates the sender monitoring DMARC reports on a regular basis. These reports would alert you to any phishing efforts made against your domain, as well as if your own email is being rejected due to DKIM or SPF failures.
Advantages
If you utilize email, DMARC is a good idea to implement.
When effective security controls against fraudulent email are implemented, delivery is simplified, brand reliability improves, and domain owners gain visibility into how their domains are being used on the Internet.
- Security: To protect consumers from spam, fraud, and phishing, don’t allow illegal usage of your email domain.
- Visibility: Gain visibility into who and what is sending email from your domain across the Internet.
- Delivery: Use the same cutting-edge technology that mega corporations use to distribute email.
- Identity: Make your email easily identifiable across the vast and increasing DMARC-capable receiver ecosystem.
Disadvantages
DMARC is capable in most cases. Phishing has become significantly more difficult as a result of technological advancements. However, although this approach solves one issue, it creates another: false positives. In two types of situations, legitimate messages can be blocked or tagged as spam:
- Messages that have been forwarded Whether messages are transferred from multiple mailboxes or diverted through intermediary mail nodes, some mail systems fail SPF and DKIM signatures in forwarded messages (relays).
- Setting is incorrect. When configuring DKIM and SPF, it’s not unusual for mail server admins to make mistakes.
How does it work?
Because DMARC is reliant on SPF and/or DKIM results, at least one of these must be in existence for the email domain. You must publish a DMARC entry in the DNS to use DMARC.
After validating SPF and DKIM status, a DMARC record is a text item within the DNS record that tells the world your email domain’s policy. If SPF, DKIM, or both pass, DMARC authenticates. This is known as identifier alignment or DMARC alignment. It’s possible that SPF and DKIM pass, but DMARC fails, based on identifier alignment.
A DMARC record also instructs email servers to submit XML reports to the DMARC record’s reporting email address. These reports show you how your email is traveling around the ecosystem and allow you to see who else is using your email domain.
Making sense of reports written in XML can be difficult, especially when there are a lot of them. The DMARCIAN platform can receive these data and visualize how your email domains are utilized, allowing you to take action and change your DMARC policy to p=reject.
Difference between SPF and DKIM
DKIM is a collection of keys that tells IPs that you’re the original sender and that your email hasn’t been tampered with. SPF is a whitelist that includes everyone who has been given permission to send messages on your behalf. If you’re eager to see how it all works, look at the email headers to see if an email is correctly signed with DKIM or passes SPF.
Why do you need SPF DKIM DMARC?
Enabling email verification isn’t only a good idea for getting your emails delivered; it’s also a crucial tool for protecting your business ’ reputation by reducing the odds that an unauthorized sender would be able to use your domain without your permission or knowledge.
Usage of SPF DKIM DMARC together?
Because of the evolution of the internet’s email protocols, we’ll need three.
The message headers (such as the To:, From:, and Bcc: addresses) were purposefully isolated from the message’s actual content. This was a benefit, but it has resulted in new worlds of suffering for modern-day IT managers.
If you properly implement all three protocols in your email infrastructure, you can assure that messages cannot be easily falsified and that they never reach your users’ inboxes.
Conclusion
In today’s world, doing email validation on your emails is critical for email delivery. Due to multiple email impersonation and breach attempts, the regulations will only become harsher in the future. Just make sure that if you’re sending emails through a certain ISP domain, you check their validation policies to see how you can get the most out of your email deliveries.
You can also check out our latest content on 7 Ways That IAM Can Protect Your Small Business



