In today’s cyber threats against sensitive data world, it is most important for organizations to ensure strong security. The penetration testing tools are the best tools for securing networks, applications, and systems. Penetration testing tools and penetration test tools help the organization in simulating real-world cyber attacks, identifying vulnerabilities before attackers exploit them, and performing risk assessments. There are several penetration load testing tools, including open-source penetration testing tools and network penetration testing tools, so IT professionals can help to assess security risks protect critical assets, and ensure compliance.
CyberPanel is used in conjunction with such tools to create a smooth environment for effective management of server security. Such tools have deployed and configured testing tool features, especially when dealing with web applications and server infrastructure in CyberPanel. This article will walk through some of the best penetration testing tools for network security and penetration load testing to help organizations harden their defenses. As a cybersecurity professional or a network administrator, this list guides you in choosing the tools that could be effective for penetration testing.
What Are Penetration Testing Tools?
Penetration testing tools are software applications or platforms that simulate an attack to determine potential vulnerabilities in systems, networks, and applications. These tools aim to reveal security loopholes that portray the level of threats and give insight into improving system defenses. Some of the common types of penetration tests include network, application, and wireless testing, for which tools exist as well. Many of these tools include network mapping, vulnerability scanning, password cracking, and exploitation which make them important in modern cybersecurity practice.
Benefits and Best Practices of Penetration Testing Tools
Better Security: detects vulnerability before an attack, and therefore, reduces the vulnerability of a security breach.
Compliance: helps businesses comply with security standards (GDPR, HIPAA, PCI-DSS).
Continuous Improvement: Open-source tools (such as the ones on GitHub) facilitate continuous updates and security enhancement.
Get exclusive access to all things tech-savvy, and be the first to receive
the latest updates directly in your inbox.
Best Practices:
Update Tool: ensures testing is being done with the latest vulnerability.
Documentation: document every vulnerability and solution for future auditing.
Use Multiple Tools: Multiple tools are used in such a manner to ensure that the approach covers the protection of all aspects: network, web, and wireless security.
Top 10 Free Best Penetrating Tools
1. Metasploit Framework
Metasploit is a big, extensible framework for identifying vulnerabilities in networks and systems along with their exploitation and validation. This tool is greatly used by cyber professionals in simulating real-time attacks to find out if and how their security measures work. It has an exploit and payload database for the launch of targeted attacks at specific identified vulnerabilities. It also supports a wide range of payloads for penetration testing and has modules for auxiliary functions such as data collection. Its community and pro versions support both beginners and advanced users, making it perfect for from hobbyists to seasoned security professionals.
Benefits:
- Exploits range
- Scripting and automation
- Easy for beginners yet very useful for advanced users
Best Practices: Tend to update the exploit database.
2. Nmap (Network Mapper)
Nmap is a network scanner and security auditing tool, used to create an overview of all the devices that connect to a network along with information on the open ports and services running on each of the devices. It can be used for big networks as well as a small scale for a deeper analysis of individual hosts. Nmap gathers information through different scanning techniques and gives an option for OS detection, service versioning, and scripting. Nmap Many individuals view Nmap as an accurate, efficient tool for network mapping, vulnerability scanning, and penetration testing.
Benefits:
- Identifies live hosts and services in a network
- Has OS detection, port scanning, and vulnerability detection
Best Practices: Make use of the installation of firewall settings to be able to track potential exposure points.
3. Burp Suite Community Edition
Burp Suite Community is an all-around comprehensive platform for web application security testing. It provides a suite that equips a tester with tools to identify vulnerabilities in web applications and exploit them. The tools include scanning web-based vulnerabilities, a proxy that intercepts and modifies traffic, and brute force passwords and bypasses protections. Known for its strong functionality, Burp Suite is excellent for finding common web vulnerabilities such as SQL injection, cross-site scripting (XSS), and session handling issues. This testing tool is very widely used for checking web applications mainly due to its friendly interface, as well as integration capabilities with third-party tools.

Benefits:
- Helps in finding common vulnerabilities like XSS, SQL Injection
- User-friendly, easy to navigate for newbies and pros as well
Best Practices: This shall be combined with Manual Testing techniques for better results.
4. Wireshark
Wireshark is a free source network protocol analyzer; it lets users have profound insight into network traffic. With real-time packet capture, one can easily examine individual packets to unravel invaluable information about network protocols, applications, or even infrastructure. Security professionals use Wireshark to trace anomalies and analyze of behavior of network systems, troubleshoot problems, or even signs of malicious activities. Wireshark serves as an invaluable tool in diagnosing and protecting network security through its robust filtering and customization views.
Benefits
- Detailed traffic analysis with data packet inspection
- Works with multiple network protocols
Best Practice: Use Wireshark to be used in conjunction with Nmap for full network exploitation
5. SQLmap
SQLmap is an automatic penetration testing tool that targets to attack and exploit SQL injection flaws across database-driven applications. It simplifies identifying SQL injection flaws, as well as providing other advanced functionalities including data fetching, which enables full remote database access, amongst others. SQLmap supports various databases; thus, it is deployed on many web applications. SQLmap achieves this by implementing a good command-line interface that is efficient in the aspect of penetration testing for developers and penetration testers.
Benefits
- Automate SQL Injection attacks
- SQL databases support a range
Good Practices: Use only permission before applying it to databases.
6. Aircrack-ng
Aircrack-ng is a suite of tools used to assess the security of a Wi-Fi network. It includes tools that monitor, capture and decrypt wireless packets. Aircrack-ng is very widely used for testing WEP and WPA-PSK networks. Aircrack-ng supports packet injection and brute-force attacks, making it very effective for penetration testing on wireless networks. By giving insights into Wi-Fi vulnerabilities, Aircrack-ng helps security professionals protect their networks and secure sensitive information against unauthorized access.
Advantages:
- These tools are particularly well suited to Wi-Fi security testing
- It also detects and listens for wireless traffic vulnerabilities
Good Practices: Use along with Wireshark for network-wide analysis.
7. Nikto
Nikto is an open-source free web server scanner. It scans possibly damaging problems found associated with web applications including old software, misconfiguring configuration files, and known vulnerabilities. Nikto scans the web servers at their all details. This makes it an excellent tool for very rapid web server assessments due to the exploitable nature of problems that it will find. The vulnerability databases are frequently updated, in addition to this light command-line interface making it easy and effective in carrying out web security assessment.
Advantages:
- Web server-focused, so great for finding HTTP vulnerabilities
- Very light and user-friendly
Best Practices: Run with Burp Suite to conduct a comprehensive web application test.
8. John the Ripper
John the Ripper is a super-fast, highly customizable password cracker that identifies weak passwords for systems. It supports almost every possible type of hash available. John the Ripper uses both dictionary attacks and brute-force attacks to crack passwords and is extremely efficient with security audits and analysis of password strength. Its versatility and power make it well-suited for penetration testers and system administrators who need to audit password security.
Advantages:
- Does support a range of password hashes
- Highly customizable and scriptable
Best Practices: Apply to test password strength on various platforms.
9. Hydra
Hydra is a login attack tool that applies network login password cracking. Several protocols are supported, including SSH, FTP, HTTP, SMTP, and so on. Hydra proves to be multidimensional when applying different network services for testing. Hydra performs brute-force and dictionary attacks through countless combinations to crack passwords and even break into systems in unauthorized manners. One of the key strengths of Hydra is its performance, flexibility, and ability to run in parallel across multiple targets; it can be used with customizable modules for fitting into a range of scenarios.
Benefits:
- Supports many protocols
- High-speed brute-force attacks
Best Practices: Use responsibly within authorized environments.
10. OWASP ZAP
OWASP Zed Attack Proxy (ZAP) is an open-source, free web application security scanner developed to assist developers and security experts find vulnerabilities in their applications. Being both friendly and efficient for both new users and heavy users, the tool applies to automatic scanning, manual testing tools, as well as all add-ons that complement it. ZAP’s passive scan is very helpful in a workflow, especially in a DevSecOps workflow since it will detect vulnerabilities without affecting the behavior of the tested application. In general, given its strong support and continuous updates, ZAP is one of the most vital and popular tools for securing web applications.
Benefits:
- Friendly interface for beginners and strong interface for experts
- Large community and supports large plugins
Best Practices: For use in workflows of DevSecOps.
How Companies Benefit From Using Top Penetration Testing Tools
Penetration testing tools adoption does not only focus on the positive aspects of security. It is also more related to better business results. Many companies are said to decline the occurrence of security incidents when these tools are implemented, which eventually means a growing level of customer trust- the bottom line of business development.
The graph below plots how the tools affect various business metrics. For each tool, three key indicators are found:
Security Posture: This is an indication that overall improvements have been found in the security measures of the companies using the tool.
Increased Trust: Percentage increase in customer trust due to these tools.
Sales Growth: Increase in sales that can be ascribed to a strengthened security posture and the resultant customer trust.
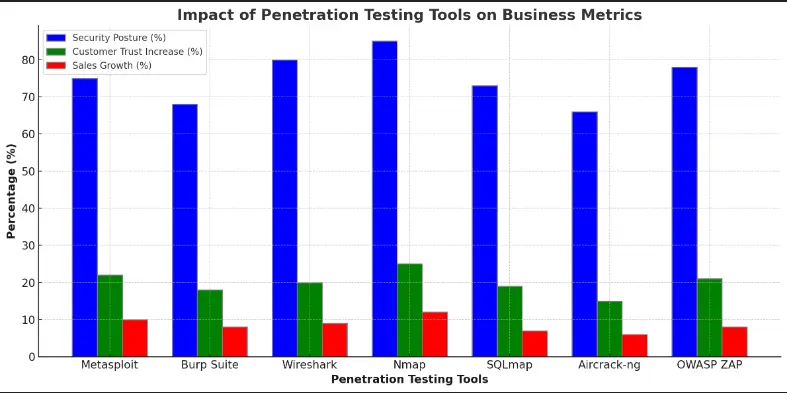
This graph will give you an idea of how the best penetration testing tools mean increased security that drives growth to your business through increased customer confidence and sales.
Role of CyberPanel In Penetration Testing & Security Management
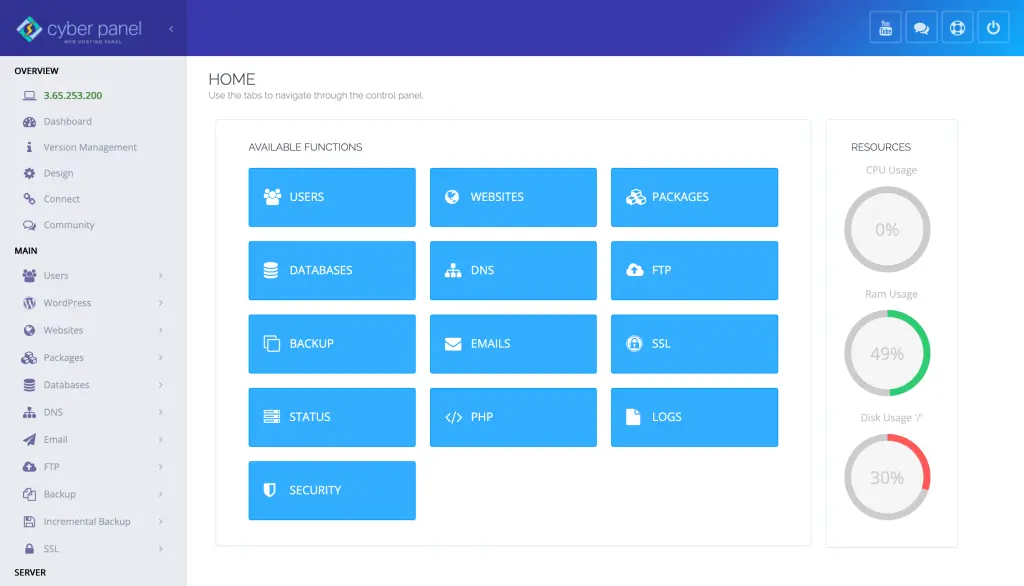
CyberPanel is a highly flexible, open-source web hosting control panel that includes a full set of tools for controlling and securing web hosting settings. OpenLiteSpeed being the foundation, CyberPanel also provides features that make servers healthier and more secure for system administrators and security experts to maintain. Here’s how CyberPanel can support penetration testing and general security management:
User Management and Access Control: CyberPanel provides the administrator with the ability to define and control access levels for different users. It makes sure that only the required people get the desired information and configurations. That is very significant important in penetration testing. With access management, vulnerabilities are protected from attacks by attackers.
Firewalls and Security: CyberPanel integrates firewall management on which users can set up security rules to stop unwanted access. This is helpful in doing network penetration testing as it avails various attack scenarios, simulates them, and shows how the firewall would react to such real threats.
SSL Management: CyberPanel supports SSL certificate installation through a one-click process that protects web applications against any sort of man-in-the-middle (MITM) attacks. Penetration testers may also use CyberPanel to test SSL configurations and validate the strength of encryption on websites.
Log Management: CyberPanel offers administrator log management features, so it is easy to draw server logs to see anomalies and possible security threats. The logs are also useful for penetration testing: log analyses provide information on possible vulnerabilities, while attack patterns can be reviewed.
Backup and Restore: This is how the CyberPanel backup and restore facility will help create secure backups that are then employed before carrying out any penetration tests, ensuring that in case anything goes wrong during the penetration test, all data can be recovered.
Integrate with other Security Tools: Such integration with all other forms of security tools enhances the detection, mitigation, and response capabilities in relation to security incidents. This makes CyberPanel a perfect component within a complete strategy of security.
DDoS Protection: It has features on CyberPanel for DDoS mitigation in which the administrator could set up his defenses against a large attack. It really helps when doing penetration testing as it simulates attacks on your server to figure out its capability to sustain high malicious traffic.
To cut it short, CyberPanel is an amazingly effective web hosting management platform with security-focused features ideal for penetration testing. The tool will give you the foundational security you need to ensure that your server is capable of standing up against possible attacks—whether network-based or application vulnerabilities.
FAQs About Penetration Testing Tools
1. What is a penetration testing tool?
A penetration testing tool is specific software used by application security professionals to identify exploit and document the vulnerabilities within the system network or web application. Therefore, these tools simulate real-world attacks that improve the security posture of an organization.
2. Why are penetration testing tools important?
Penetration testing tools are vital in the proactive discovery of security vulnerabilities within systems. While they reveal such vulnerabilities, organizations can patch out the weaknesses before attackers exploit them to breach data, lowering the risk involved.
3. What are the best penetration testing tools for beginners?
Recommended penetration testing tools for beginners often include Metasploit, Nmap, and Wireshark since they provide interfaces that are pretty user-friendly plus vast amounts of online resource materials that will aid learning.
4. Are open-source penetration testing tools safe to use?
Free open-source penetration testing tools are generally safe if used responsibly by a professional. It is merely to let people download trusted versions of such tools and understand that misuse can land one in legal hot water.
5. What are the best practices for using penetration testing tools?
Some of the good practices that characterize the use of penetration testing tools are the following: appropriately setting clear objectives, testing in a controlled environment, keeping records, getting permission from the people whose systems are to be tested, following legal guidance, and testing according to a schedule to maintain your systems.
6. How frequent should the pen testing be?
Optimal penetration testing should be performed once a year or after critical changes are made to the infrastructure. Most critical sectors and changed IT environments ought to be tested more often, attuned to the latest threats in the system.
Culmination: Safe under the best penetration testing tools.
To sum up, Penetration testing tools are the most valuable asset in the modern digital environment. It helps organizations to find and mitigate vulnerabilities proactively. Right from the versatile tool Metasploit to powerful brute-force utilities such as Hydra, penetration testing software keeps security teams at the top of potential threats. This can be achieved by appropriate server management and security with the help of CyberPanel, thereby developing a well-protected infrastructure against the current cyberattacks.
It’s the right mix of tools and practices that make all the difference in safeguarding your digital assets. Discover the power of penetration testing tools and take control of your organization’s security strategy today.
Begin with CyberPanel, creating a secure, resilient web hosting environment that protects your network from unwanted intrusions!



