Malware threats are evolving rapidly. Malware analysis tools are essential for identifying, examining, and eliminating these threats.
According to recent statistics from multiple resources, 560,000 new malware are detected DAILY!
Malware analysis is a process that involves dissecting, examining, and understanding the functionality and intent of malicious software. Helping security specialists gain insights into malware behavior, develop effective countermeasures, and enhance security across networks, applications, and endpoints.
To do all this, security specialists use Malware analysis tools. As, New technologies like artificial intelligence (AI) have allowed hackers to attack more cleverly. In response, security measures are also evolving to counter malware threats.
This guide will explore top tools for both experienced and beginner security professionals, helping to protect systems and improve threat detection. We’ll discuss how these tools enhance efficiency and accessibility in malware analysis.
What is Malware Analysis?
Malware Analysis uses sophisticated methods to find, examine, and remove harmful software threats. It involves an in-depth examination of the distinct characteristics, goals, origins, and possible impacts of malicious software and code, including spyware, viruses, malvertising, and ransomware. It delves into the malware code to learn its differences from other types.
Get exclusive access to all things tech-savvy, and be the first to receive
the latest updates directly in your inbox.
Malware Analysis Tools in Dealing with Incidents and Finding Threats (Real-World Use Cases)
- Malware analysis helps respond quickly to incidents by providing important information about existing and future attacks.
- It supports research and malware detection, helping spot harmful code and how it differs from harmless code.
- Through malware analysis, we can pull out indicators of compromise (IOCs) to see how malware might attack a system, which helps in spotting future attacks.
- Threat hunters rely on malware analysis to find unknown cyber threats, like a honey trap, and potentially uncover new dangers.
- Malware analysis tools can also send alerts and rank them by their seriousness, letting security teams focus on the biggest threats first.
3 Types of Malware Analysis
Each step of the intricate process of malware analysis helps improve the malicious program’s clarity. The phases of malware analysis fall into the following categories:
Static malware analysis
Static malware analysis checks for files that could harm your system without actually running the malware. This makes it a safe way to find harmful libraries or packed files. It can reveal details about the malware, like filenames, hashes, IP addresses, domains, and file header info. You can use different tools, like network analyzers, to look at the malware.
Dynamic malware analysis
Dynamic malware analysis uses a sandbox, which is a safer, isolated virtual space where you can run suspicious code. Security experts can keep a close eye on the malware in the sandbox without risking infection to the rest of the system or network, helping them gather more info about the malware.
Hybrid malware analysis
Hybrid malware analysis mixes both static and dynamic methods. For example, if the harmful code changes something in the computer’s memory, dynamic analysis can catch that. Then, static analysis can figure out exactly what changes happened.
What Features should you Look for in Malware Analysis Tools?
A reliable malware analysis tool must have the following features to protect your systems efficiently.
- Real-Time Analysis: To keep ahead of attackers, tools use real-time analysis of data and actions. Malware has less time to infiltrate your systems.
- Static and dynamic: Tools should provide both static and dynamic analysis to provide thorough insights.
- Sandboxing Capabilities: These enable the execution of dubious files in a separate setting so that malware activity can be analyzed without risking your network.
- Integration with Threat Intelligence: To stay current on known threats and new malware patterns, it connects to international threat intelligence databases. You can encounter both new and existing threats.
- Customizable Reporting: Allows comprehension of communication, defense tactics, and threat details. By keeping a record of your security measures.
- Automated Detection: Time is saved via automated detection and analysis, which finds and evaluates risk alerts without any need for human intervention. Especially in larger organizations.
- Multiplatform Support: Provides complete protection for every device.
- User-Friendly Interface: Makes sure that beginner security experts may quickly follow and operate it effectively.
Top 5 Malware Analysis Tools for 2025 (Overview of Each Tool (Features, Pros, Cons, Pricing)

There are dozens of tools for Malware Analysis but We’ve picked the 5 best Malware Analysis Tools out of them. Take a look at the following:
Tool 1: VirusTotal
VirusTotal is an international IT security platform. Blue team employs this malware analysis tool extensively to examine harmful files and URLs. This includes SOC analysts, incident responders, threat hunters, security researchers, and malware analysts.
- Makes use of more than 70 URL/domain blocklisting providers and antivirus scanners.
- For user convenience, a variety of file submission options are provided.
- Examining submitted material advances international IT security standards.
- The submitter, examination partners, and community are informed of the results.
- Offers insightful information to security product creators and cybersecurity experts.
- Offers a community for sharing notes and commenting on files and URLs.
- Customers of VirusTotal Premium get access to sophisticated tools for intricate, criteria-based searches.
Tool 2: Cuckoo Sandbox
Cuckoo Sandbox is now one of the best malware analysis tools for behavioral analysis. It is an open-source, automated malware analysis tool that works with Linux, macOS, Android, and Windows.
How do the Features work?
- Examines harmful files and websites on systems that are virtualized.
- Easily understands file activity and API requests by tracking them.
- Even with SSL/TLS encryption, network traffic is dumped and examined.
Its open-source and modular design enables customization of the analysis environment, results processing, and reporting. - It can be hosted in several places for a smooth connection with existing frameworks and backends.
- It does sophisticated memory analysis using Volatility and YARA.
Tool 3: Hybrid Analysis

Hybrid Analysis is a comprehensive malware analysis tool that employs Falcon Sandbox and Hybrid Analysis technology to conduct thorough static and dynamic examinations. This platform can analyze even the most mysterious malware by combining runtime data with memory dump analysis.

How do the Features work?
- Indicators of compromise (IoCs) and behavior indicators are extracted.
- Detects and investigates unknown threats using hybrid analysis techniques.
- Users can upload and share collections of files for analysis using antivirus engines, reputation lookups, and machine learning.
- Hybrid Analysis provides a large searchable database with more than 767 million IoCs.
- Makes it possible to hunt malware samples by matching strings and hex patterns or by utilizing YARA rules.
- Both a free and a premium version are accessible.
- The premium version can scan hundreds of files, whereas the free version can only scan up to 20.
Web service, API, load balancing controller, runtime monitors, hybrid analysis technologies, report generator, indications, and scripts and signatures are all included.
Tool 4: IDA Pro
IDA Pro is a malware analysis tool that Software analysts, reverse engineers, malware analysts, and cybersecurity experts all frequently utilize IDA Pro. Is a top binary code analysis tool. It examines binaries in a matter of seconds and comes with a robust disassembler and a flexible debugger for a complete analysis solution.
How do the Features work?
- Is an extensive tool for Analyzing the Binary Code of malware.
- Utilized by software analysts, reverse engineers, malware analysts, as well as cybersecurity professionals.
- Comes with a disassembler and debugger for thorough analysis.
- Converts machine-executable code to assembly language source code for human-readable code.
- Backs various debugging objectives and offers debugging abilities across different platforms.
- Provides a dynamic setting for swift decision-making or instinctive examination.
- Completely customizable with a strong macro-like language for automating tasks.
- Works with a variety of file formats, processors, and platforms.
- Unlocked plug-in design for simple expansion of features.
- Provides support for different operating systems such as Windows, Linux, and macOS.
Tool 5: PeStudio
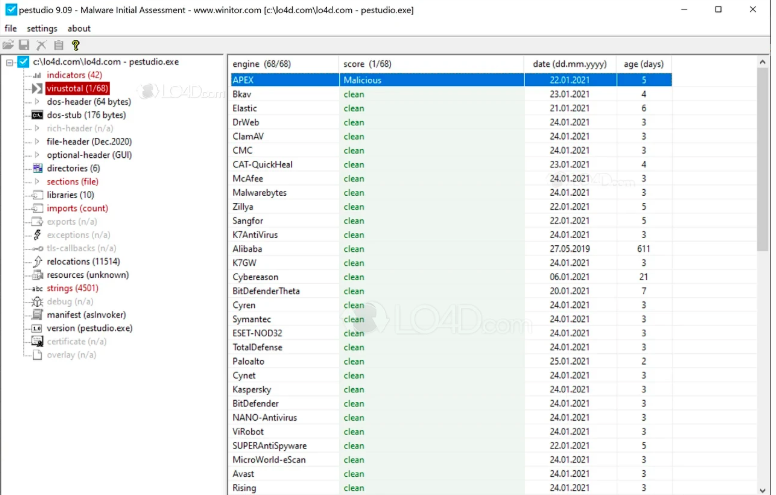
PeStudio is an excellent malware analysis tool. With the help of this great tool, security analysts can immediately identify any suspicious artifacts and do an initial analysis of a malware file.
How do the Features work?
- Analyzing malware includes uploading a binary file, sharing hashes, and checking for detections in VirusTotal.
- While packed samples may not produce significant indicators of compromise, analyzing the strings after unpacking can reveal valuable details such as malicious domains and IP addresses.
- The ‘Entropy’ of the malware assists in determining whether it is compressed, showing a level of code hiding its genuine purpose.
- PeStudio shows the file’s entropy level, with 8 being the top, suggesting the presence of compressed malware.
- The tab labeled ‘Imports’ includes features that have been brought into the malware for particular purposes.
- Malicious software can adopt the same approach as genuine programs, like Windows’ DLLs, to incorporate its features.
- Studying imports can assist in forecasting possible malicious activities on systems such as Windows, Linux, and macOS.
How to Use Malware Analysis Tools Effectively?
Here’s a simple overview of how you can do malware analysis using these powerful tools. Step-by-step guide!
- Send the tool the dubious file or URL.
- Examine the analysis report to see whether any dangers were found.
- Act on the insights by patching vulnerabilities or restricting IPs, for example.
- Experts’ Best Practices:
- Construct a SIEM (Security Information and Event Management) system with integrated tools.
- Make use of several tools for cross-checking.
Major Drawbacks of Malware Analysis
Here area some major challenges faced by security professionals when analyzing malware.
- Malware analysis often takes a significant amount of time and necessitates expertise and specific tools.
- Infection Risk: Analyzing malware in an uncontrolled setting may spread the malware and damage other systems.
- Organizations may find it costly to obtain and uphold the specialized tools and expertise needed for malware analysis.
- Malware is always changing, making the analysis task difficult, and needing specific knowledge and skills.
- Incorrect detections, Sometimes, analyzing malware can lead to incorrect detections, causing false alarms and undermining trust in the current security measures.
Key Takeaways for Security Professionals in 2025
If you’re a security expert employing the best malware analysis tools to examine malicious files is a vital resource. Regardless of your level of experience, you can safeguard your systems and data from changing threats by investing in the appropriate technologies.
This article reviewed how malware analysis is important, the top 5 malware analysis tools, and how each tool’s features work in detecting and fixing malicious files or security breaches. Even when they’re so useful, what challenges do organizations face today?
Final Suggestions
- Start with VirusTotal for fast scans.
- Invest in programs like IDA Pro or Cuckoo Sandbox for more complex analysis.
- Give preference to tools that fit in well with your current workflows.
We also have a detailed video on Malvare analysis tools, just for you!
FAQ’s
1. What is malware analysis, and how does it work?
Examining malicious software to determine its origin, behavior, and effects is known as malware analysis. Studying its code, features, and methods of system intrusion are all part of this. The objective is to find weaknesses, reduce threats, and fortify cybersecurity defenses in general.
2. Are Cyberattacks Preventable by Malware Analysis Tools?
Certainly! They identify threats, evaluate them, and offer insights to prevent harm before it occurs.
3. Are Malware Analysis Tools Free?
Of course! Free choices are available for both novices and experts using programs like VirusTotal and Hybrid Analysis.
4. Which Are the Best Malware Analysis tools to use in 2025?
VirusTotal, Cuckoo Sandbox, and Hybrid Analysis are the top choices because of their efficiency and speed.



