In today’s world of rapid change and technology, it has been found that the Docker platform is one of the popular containerization platforms that makes it easy for developers to build, deploy, and run applications with a level of efficiency that has never been seen before. As Docker continues to grow, so does the entire palette of security concerns that organizations need to address to keep their applications and data secure. This guide explores the best practices and common security issues that surround Docker container security.
Understanding Docker Security
What is Docker?
Docker is an open-source platform. It automates the deployment of applications in portable containers. Containers include an application and its dependencies to make sure it runs consistently across different environments. Although Docker increases productivity and workflow effectiveness, it also introduces some unique challenges in terms of security.
Why Docker Security is Important
In a modern world where organizations are constantly moving to containerized applications, security has to be intensified. Docker security is the protection of container infrastructure, the applications kept within the containers, and the data from these applications. There will then be wide avenues for vulnerabilities that create exposure to attacks, data breaches, as well as issues concerning compliance once it cannot be prioritized.
Common Docker Security Concerns:
Beginning with securing Docker involves getting an idea about the security threats. Here are some of the common Docker security concerns-
1. Insecure Images
An image is used as a building block to create a container. If the image is pulled from an untrusted source, then there could be vulnerabilities or malicious code. Insecure images might expose your systems.
2. Container Isolation Weaknesses
While containers do provide a level of segregation, they are all on the same kernel of the host OS. When the kernel gets breached, hundreds of containers could be hacked at once. This is one of the most significant threats to the entire environment.
Get exclusive access to all things tech-savvy, and be the first to receive
the latest updates directly in your inbox.
3. Network Security Issues
Containers generally run on an environment shared by a network. With this factor, some communication between them may be intercepted or changed by hackers, leading to the possible breach of data.
4. Management of Secrets
It is challenging to handle sensitive information like API keys, passwords, and certificates in containers in several ways. Hard coding or storing them insecurely might result in exposing sensitive information.
5. Resource Limitations
Containers may consume a lot of resources than expected, and this may contribute to denial-of-service (DoS) attacks. Proper resource limit configuration ensures stability and safety.
6. Runtime Attacks
Attackers may target running containers to exploit vulnerabilities, access sensitive data, or launch attacks on other services within the same environment.
Docker Security Best Practices
To ensure excellent Docker security, it is mandatory to practice best practices. Here are a few best practices:
1. Use Official Images
Always pull Docker images from the official source, say, Docker Hub. These are often scanned regularly, so the chances of vulnerability are less.

2. Scan Images for Vulnerabilities
Use some tool like Trivy or Clair to scan the Docker images regularly for known vulnerabilities. This detects potential issues before these applications are deployed.

3. Run Containers without Root
Containers by default run as the root user in Docker. As best practice, update your Dockerfile to obtain and launch the containers under a non-root user.

4. Containers without Unwanted Capabilities
To limit what the containers can do, use the –cap-drop and –cap-add options available with Docker commands. Just add capabilities that are not required for the execution of your application.

5. Readonly Filesystems
If possible, initialize the filesystem of your containers to be read-only. This will prevent any changes in your filesystem by unauthorized users.


6. Network Segmentation
Docker networking capability lets you have completely isolated networks for each of your containers. This therefore means that communication can only be made solely to necessary services.
7. Maintenance Updates
Both Docker itself and your container images should periodically receive maintenance updates. Most security patches are released to plug known vulnerabilities.
8. Limit Resource Usage
Control resource usage for your containers. This is important to prevent any single process from consuming more than its fair share of resources on your host. To reduce denial-of-service attacks in particular: you can limit them.
Solutions To Docker Security Issues
1. Role-Based Access Control (RBAC)
Docker supports RBAC functionality, and this enables you to establish roles and permissions so that users can only do what is required for the role assigned to them.
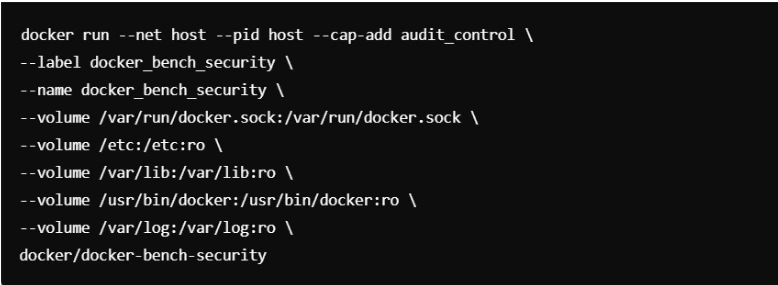
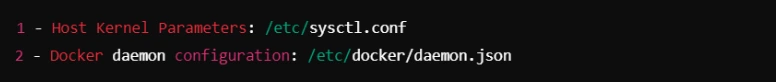
2. Docker Bench for Security
Docker Bench The Docker bench is a script that performs common best practices in Docker containers and presents a security report.
3. Secure Networking
Make use of the network capabilities of Docker to generate secure isolated networks for your containers. Use encrypted connections wherever possible to protect data in transit.
4. Continuous Monitoring
Use logging and monitoring solutions like ELK Stack or Prometheus to track the activity happening at the container level, and catch anomalies in real-time.
5. Regular Backups
Ensure you have a good schedule for backing up your containers and data. That may help in quick recovery following a security incident.
6. Container Orchestration Security
If you are using a container orchestration tool, such as Kubernetes, you should secure your orchestration environment. Observe the least privilege principle with controls over access and network policies.
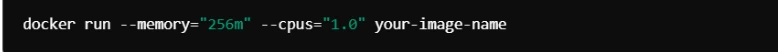
7. Limit Container Resources
Use resource limits to prevent containers from consuming excessive resources.
Role of CyberPanel in Docker Security
CyberPanel is a web hosting control panel that provides support for Docker. With the help of CyberPanel, you can control your containers more effectively. Here’s how CyberPanel helps in Docker security using its best Docker management:
1. User Management
CyberPanel develops an easy interface for the various customer roles and permissions, thereby minimizing the chances of an unauthorized access issue. You may also create unique roles with preferred permissions.
2. Image Management
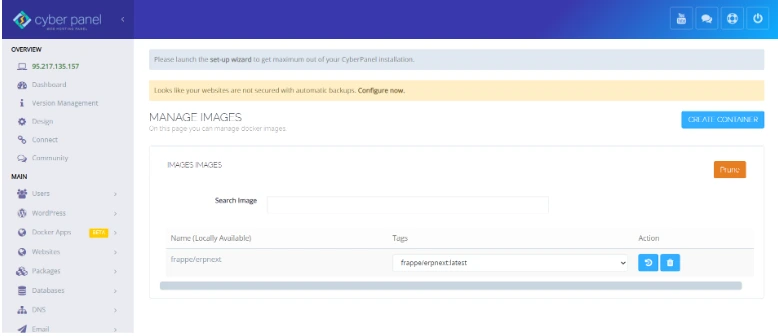
Easy Management of Docker Images from CyberPanel. The trusted image will only be deployed in your environment because of the easy management of Docker images from CyberPanel.
3. Integrated Monitoring
Generally, CyberPanel supports very good integration with the monitoring tools for getting insights about container performance and security status. Controlling logs and metrics is easy through the dashboard.
4. Firewall Configuration
This control panel simplifies the configuration of firewall settings, enhancing the security of your network by blocking all unwanted traffic.
5. Automated Backups
CyberPanel has an automated backup provision that will save your container data regularly and ensure the quickest restoration in case of a security incident.
Recommendations for CyberPanel Users
1. Update CyberPanel
Just like updating your Docker images, always update CyberPanel itself. The improvement of the environment’s security aspect comes in the form of security patches as well as feature updates.
2. Use HTTPS
Always use HTTPS for the CyberPanel to secure communications and to protect sensitive data from intercepting.
3. Monitor Access Logs
Verify access logs for any unapproved access to the CyberPanel interface or Docker containers.
4. Utilize CyberPanel Plugins
Scour around for available plugins of CyberPanel meant to boost security through integration with capabilities like surveillance, backups, or firewalls.
5. Educate Your Team
It’s also important that the team members working with Docker and CyberPanel have their security best practices with them, including training for regular exercises, to minimize the effect of human error when a security breach occurs.
1. What are the significant security threats?
Docker is exposed to a majority of the risks due to vulnerabilities in images, the breakout of containers, and insecure APIs. Configurations and good security practices can reduce such threats.
2. How Do I Protect My Docker Containers?
You can protect the Docker containers with carefulness by using only official images, running the containers under the standard account, running vulnerability scans on the container, and implementing network segmentation.
3. Which tools do you recommend for Docker security?
Trivy for scanning vulnerabilities, Docker Bench for Security, and then monitoring solutions, such as Prometheus or Grafana.
4. Is there any compliance requirement that needs to be addressed by
Docker security? Specifically, PCI DSS and HIPAA are standards that require particular security measures when you use Docker for sensitive applications.
5. How does CyberPanel secure Docker?
CyberPanel increases Docker security with respect to user management as well as with the interlocking of monitoring and easy setup for configuration of firewall settings.
Closing Thoughts: Making Your Docker Security Stack Stronger
Finally, protecting your Docker environment has never been more important at this moment and age when digital threats have become a looming specter. One of the proactive approaches to be adopted is verified images, enforcing the principle of least privilege, and conducting in-depth vulnerability assessments to build a strong defense against potential risks.
Tools like CyberPanel give the power to your security framework to streamline user management and enhance monitoring capabilities. One should realize that security is an ongoing journey that continuously demands high vigilance, timely updates, and keeping your team educated.
Want to lift your Docker security game? Implement these best practices starting today and see the power of CyberPanel in managing containers efficiently. Find out more about how CyberPanel can help you get ahead with our website or connect with us now.



