In this guide, I’m helping you choose between Ingress vs Egress Kubernetes and explain how they work and what features they offer.
What Is Ingress in Kubernetes?
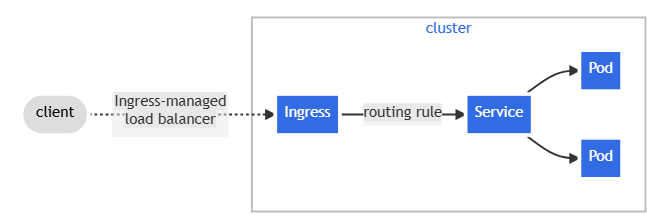
Kubernetes Ingress is an API object that enables developers to expose their applications and manage external access by providing HTTP/S routing rules to services within a Kubernetes cluster.
An Ingress acts as an entry point for incoming traffic into a system or platform. It provides a way to manage and control the routing of external requests to the appropriate internal services or resources. The Ingress is responsible for analyzing incoming requests based on predefined rules and forwarding them to the correct destination within the system.
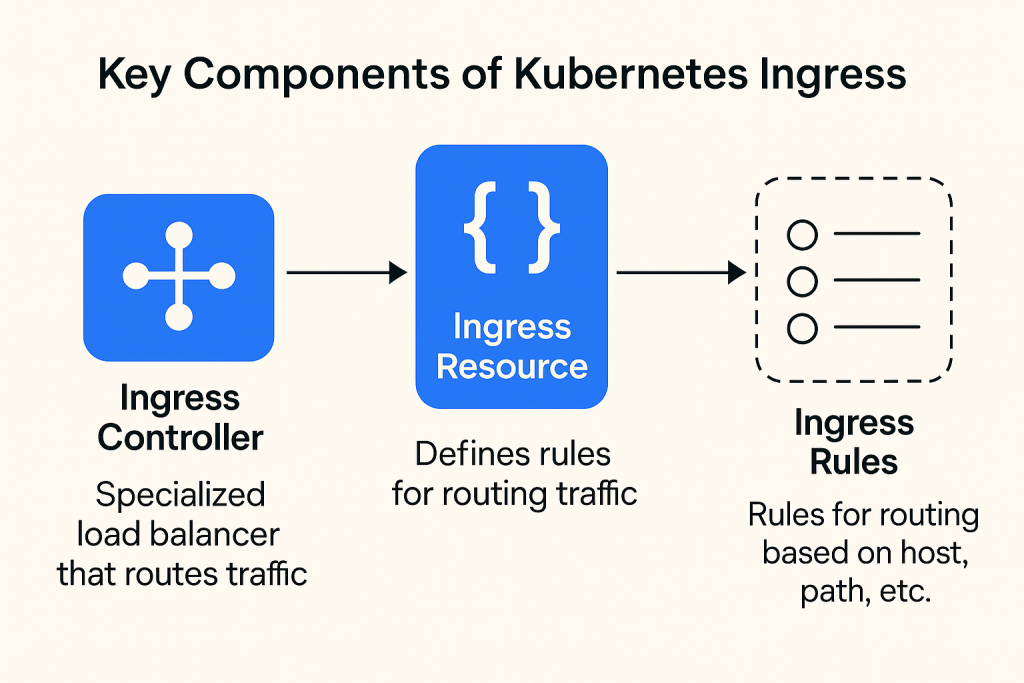
If no rules are specified, all traffic will be sent to a single default backend, which is conventionally a configuration option of the Ingress controller and is not specified in your Ingress resources. This method, also known as the DefaultBackend, is the backend that should handle requests in that case.
How does Ingress route external traffic?
- The ingress gateway serves as a network element positioned at the boundary of the mesh, managing incoming traffic.
- The routing rules, collectively known as Kubernetes ingress, dictate how external users can access services hosted within a Kubernetes cluster.
- In a standard Kubernetes application, a load balancer functions outside the cluster, while pods operate within it. Upon receiving connections from the internet, the load balancer channels traffic to an edge proxy situated inside your cluster.
- This edge proxy then directs the traffic into your pods. Often configured using ingress resources in Kubernetes, the edge proxy is commonly referred to as an ingress controller. However, it can also be set up using custom resource definitions (CRDs) or annotations.
Example:
- For data handling, direct traffic to api.company.com.
- For user engagement, direct traffic to app.company.com.
- At the Kubernetes ingress layer, handle HTTPS requests using a single TLS certificate.
Benefits
Kubernetes Ingress Benefits
Get exclusive access to all things tech-savvy, and be the first to receive
the latest updates directly in your inbox.
- Consolidates traffic routing, load balancing, and secure access for managing external services.
- Crucial for deploying and overseeing production-ready applications in Kubernetes settings.
- Facilitates load balancing, manages SSL/TLS termination, and supports name-based virtual hosting.
- Eases the management of intricate applications by directing traffic according to URL paths.
- Useful for canary deployments, progressively directing traffic to new service versions for testing.
What Is Egress in Kubernetes?
Kubernetes egress vs ingress refers to the communication that occurs from a pod to an external endpoint, allowing it to connect with services outside the cluster, since pods are automatically isolated from the external network.
Egress traffic allows connections to outside services like databases, APIs, and other services beyond the cluster.
In a Kubernetes cluster, pods are automatically isolated from the external network, preventing them from connecting to outside services.
Here’s what Egress Kubernetes Controls:
- The Egress gateway is a network element located at the edge of the mesh that manages egress traffic.
- The phrase “ingress traffic” refers to the data flow entering a cluster from an outside source to a pod. Incoming HTTP or HTTPS requests directed at a Kubernetes cluster are typically called “ingress traffic,” and this traffic is usually managed by an ingress controller.
- Egress traffic is the data that exits a cluster, moving from a pod to an external target. This includes accessing outside services like databases, APIs, and other resources not included in the cluster.
- For a Kubernetes cluster to function properly, it requires both types of traffic. To ensure the cluster remains secure and accessible, both must be configured and protected correctly.
Ingress vs Egress: What’s the Difference?
The Ingress Path
Ingress refers to traffic aimed at a workload operating within your data center or cloud. This traffic originates from an entity outside your network boundary.
Typically, ingress traffic is either untrusted or lacks identity. It may consist of rogue traffic that requires filtering or trusted traffic that needs to be routed correctly with appropriate controls.
Depending on the network boundary you define, ingress vs egress Kubernetes traffic can be either trusted or untrusted.
For instance, in a Kubernetes pod, all traffic received by the pod is considered ingress traffic for that pod. Likewise, all traffic received within a Kubernetes Cluster is ingress for that cluster.
In the context of cloud computing, all traffic received by Cloud Infrastructure, such as a public load balancer, represents the ingress layer for that cloud.
A CDN likely serves as the front for the cloud infrastructure that constitutes the ingress for Internet traffic.
The Egress Path
When a workload in a Kubernetes pod communicates with another pod, this is classified as egress traffic for that pod.

Cluster egress encompasses all traffic exiting the cluster.
A workload may also interact with external entities over the Internet. These entities could be outside the Kubernetes Cluster, Cloud Data Center, or Private Internet.
Understanding where the traffic originates is crucial for a better grasp of ingress and egress. For a Kubernetes Pod running a workload, if it initiates traffic, all responses it receives are treated differently from other untrusted ingress traffic.
In general, ingress pertains to traffic that may be subject to ingress policies, which can either be bypassed or reduced for egress or traffic initiated by egress.
Ingress vs Egress Kubernetes: Security
Data loss can occur when an ingress connects to an internal workload, and the response contains sensitive data. Loss can also happen in egress scenarios when an internal workload initiates a connection and transmits sensitive information.
Common instances of egress data loss include sending emails or uploading data to the
Kubernetes Ingress vs Egress Network Policies: Examples
Ingress YAML
apiVersion: networking.k8s.io/v1
kind: NetworkPolicy
metadata:
name: allow-frontend-ingress
spec:
podSelector:
matchLabels:
role: frontend
ingress:
- from:
- ipBlock:
cidr: 0.0.0.0/0
ports:
- protocol: TCP
port: 80
Egress vs Ingress Kubernetes YAML Example:
apiVersion: networking.k8s.io/v1
kind: NetworkPolicy
metadata:
name: restrict-egress
spec:
podSelector:
matchLabels:
role: backend
egress:
- to:
- ipBlock:
cidr: 34.102.136.180/32 # Only allow a specific IP
ports:
- protocol: TCP
port: 443
Who’s Better At Securing Your Cluster?
When it comes to Ingress vs egress Kubernetes, it not either/or, IT’S BOTH! Yes! To secure your Kubernetes cluster, you often require both working simultaneously as a team. Together, they create a controlled, observable, and secure flow of traffic that keeps your workloads safe and your production or microservice operations seamless. Or even experimenting in Dev.
Focusing on one will leave gaps.
If you’re only focusing on one, you’re leaving gaps. So It is recommended to build Ingress rules, define precise Egress policies, and then use them together with monitoring and alerts.
FAQ’s
1. Is Ingress required to expose services in Kubernetes?
No, but for security and flexibility, it’s better than exposing through NodePort or LoadBalancer.
2: Is it possible to combine the Ingress vs Egress Kubernetes rules?
Indeed, they are necessary for complete network segmentation and work well together.
3: Which is safer, ingress vs egress Kubernetes?
Both are essential. Egress stops data leaks; Ingress stops exposure.
4: Is a service mesh required for egress control?
Not all the time. While network policies are effective, service meshes offer TLS for egress traffic and deeper observability.
5: Is it possible to prevent a pod from accessing the internet altogether?
Indeed. Either by eliminating NAT routes from the node or by using egress policies.



