Security, today, is of utmost concern for individuals and institutions around the globe with increased connectivity in the digital world. However, when you have a personal server or an enterprise network, firewalls are one of the most important means to protect your system from those malicious attacks.
A Linux Firewall is important for monitoring and controlling the flow of network traffic. The firewall defines rules as traffic entering and leaving a server by validating that access to the network should only be given to authorized users and services, stopping those harmful traffics destined to breach the security of your system. Linux is reliable and versatile; hence, it has powerful tools within the firewall, which work with two primary tools: namely iptables and firewalld, to keep your system safe from all cyber threats.
In this article, we will ensure you get an in-depth idea of how to configure your Linux firewall, how you can manage your Linux firewall settings, get to know about the configuration options in Linux for firewalls, and understand exactly how CyberPanel makes it easier for you.
Let’s dive in!
Linux Firewall
A Linux firewall is a network security device that monitors and controls the flow of incoming as well as outgoing data across your network, filtering based on some predefined security rules. That is, it acts essentially like a kind of barrier between your internal system and the potentially threatening outer world, such as the internet. It ensures that only trusted connections are allowed while allowing others to block disallowed connections.
Linux firewalls use iptables and firewalld as their core firewall systems:
Get exclusive access to all things tech-savvy, and be the first to receive
the latest updates directly in your inbox.
Iptables: This is a low-level tool where users are allowed to define rules for managing network traffic. Iptables can be quite flexible and granular in control.
firewalld: This will be considered a higher level firewall service that manages iptables in easier and more organized manners by grouping services into zones. Users would be able to configure and manage them in much easier ways than through iptables.
Both tools are powerful and, in correct usage, will be able to provide adequate security levels for the Linux system. Properly configured firewalls allow for reaching robust security without unauthorized access and upholding the integrity of a network.
Why Do We Need Linux Firewall Configuration?
Properly configured Linux Firewalls are important for most server or network implementations. Their use lies in filtering and blocking unwanted traffic coming towards the network, protecting vital data, and common cyber threats, especially DDoS and unauthorized access.
If not configured properly, external attacks can still find a way into your server through your exposed sensitive services which are open on the free internet. Malicious people can enter your system through a misconfigured firewall which might compromise other things also, not only your data but services running in your network.
The configuration of a Linux firewall controls access. It determines who can access the system and under what conditions.
- Lock down the resources: To avoid unwanted and malicious traffic that destabilizes your system.
- Optimize Network Performance: Allow access only to those services necessary for reducing your network traffic load.
- Protect against attacks: Prevent common attack vectors, like DDoS and port scanning attacks.
An example is the web server, which accepts HTTP and HTTPS requests. Such a server can be compromised if other ports such as 21 (ftp) or 3306 (mysql) are open with no security measures in place. The firewall strategy is good in allowing only necessary ports and protocols to be open while closing others.
Linux Firewall Configuration
Linux firewall configuration can be done either through iptables or by firewalld. Here is a guide on how to handle your firewall configurations using either of these tools:
Linux Firewall Configuration with iptables
Step 1: Installing iptables
Usually, iptables are already installed in most Linux distributions. But, it is better to confirm if they are ready to use. You can install it by the following command:

Step 2: Check Existing Rules
Before configuration, it is important to review the current rules in place:


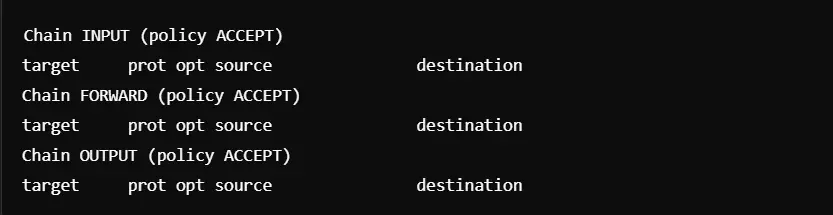
We have to tighten the rules so that the system cannot accept all incoming and outgoing traffic which is not secure.
Step 3: Block All Incoming Traffic
You have to run the following command to block all incoming traffic SSH (port 22) to remove access:
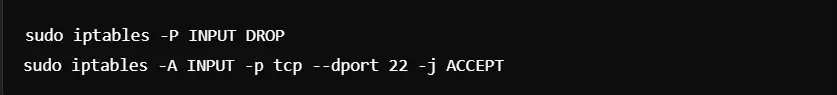
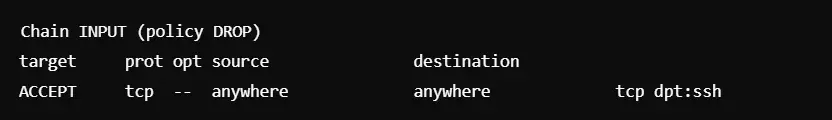
This process will protect your server from unauthorized access. However, it still allows your remote management.
Step 4: Allowing Specific Ports
It is best if your server is hosting a web application.
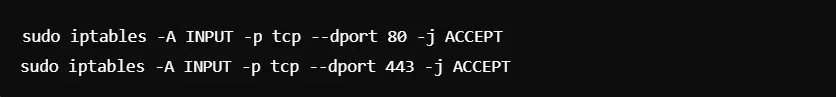
By doing this, only HTTP and HTTPS traffic is allowed in addition to SSH.
Step 5: Saving iptables Rules
You can save your iptables rules with this command:

Configuring Linux Firewall with Firewalld
Now, we are going to configure the Linux firewall with firewalld.
Step 1: Install Firewalld
You can install it with the following command:

Step 2: Check Firewall Status
You can check firewall status is running by this command:


Step 3: View Available Zones
Zones categorize and restrict traffic. You can list available zones with:

Step 4: Setting Default Zone
Now, you have to set your system’s default zone to public:
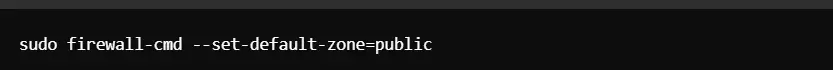
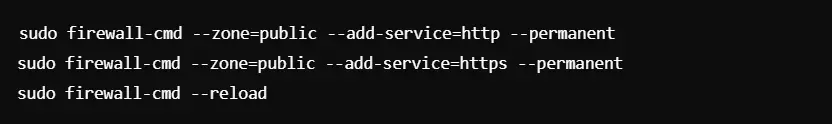
Step 5: Allow Services
You can use the following command to allow services such as HTTP and HTTPs:
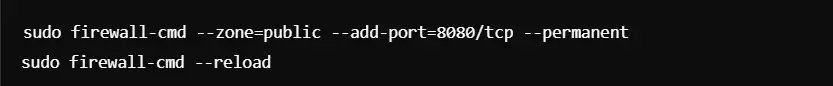
You can also add ports manually. For example, to open port 8080:
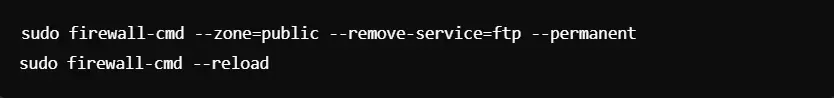
Step 6: Block Services
You can use the following command to block unnecessary services or ports:
The Role of CyberPanel in Linux Firewall Management
CyberPanel is an intuitive web hosting control panel that allows easy management of the services and server. Its greatest advantage lies in making firewall management simple, easy, and able to view, add, or remove rules without digging into terminal commands or configurations.
Benefits of Using CyberPanel in Managing Firewalls
Some benefits include:
- Visual Rule Management: One may see and manage firewall rules directly in the CyberPanel interface to only allow necessary traffic to pass through.
- Monitoring: CyberPanel has tools that help flag suspicious traffic or any security risk, always helping one maintain an optimal configuration for the firewall.
- Simplified Firewall Configuration: For those who avoid command-line interfaces, CyberPanel offers an easy way to manage the configuration of iptables and firewalld.
- CyberPanel integrates with firewalld: So you don’t have to understand complex commands in order to make alterations to the behavior of your firewall. It might be adding a service, removing a port, or searching through traffic logs; all this should be possible for you at CyberPanel.
Step-by-Step Instructions on How to Set Up Firewalls with CyberPanel
Step 1: Access the CyberPanel Dashboard
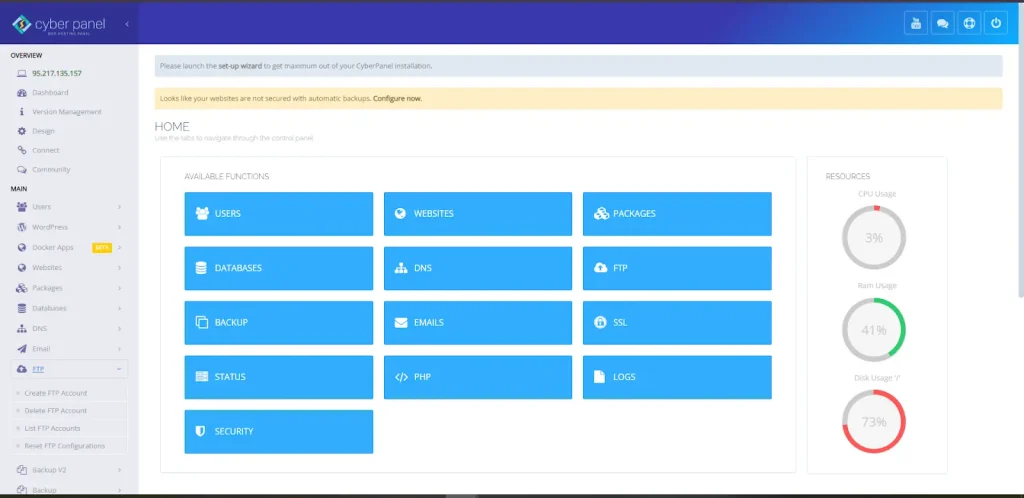
Open your browser and gain access to your dashboard with CyberPanel. Now, Log in using admin credentials.
Step 2: Firewall Section
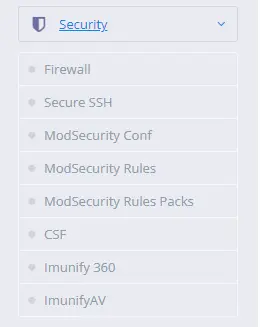
After you log in, scroll down to find the sidebar on the left-hand side. Now, find the Security section. Inside this section, click on this to expand all options. There should be an option called Firewall; click on this. This will get you into your firewall management section.
Step 3: Add New Firewall Rules
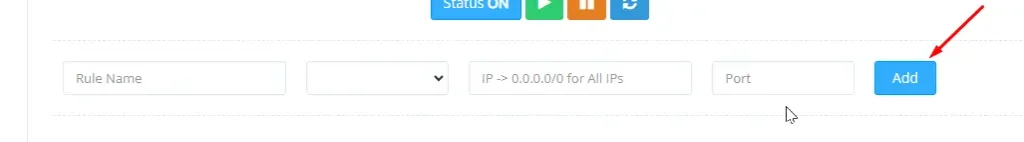
Under the Firewall section, you will see some listed existing firewall rules (if there are any). Now click Add New Rules to create a new one.
Step 4: Setup Firewall Rule
You are prompted to fill out details for your new rule.
- Protocol: Choose your network protocol from the dropdown menu. There’s TCP and UDP. Most of the time, HTTP and SSH utilize TCP.
- Port Range: Type in the port number or range of ports you would like to allow or deny access.
- Source IP (Optional): You can restrict the incoming traffic from a particular source of IP address or a pool of addresses in case you only need a specific IP address or range of IP addresses; otherwise, you can leave this field empty if you need to allow the blocking of traffic from all IP addresses.
Step 5: Save the Firewall Rule
Upon filling in all the required fields, you can save the rule by submitting it, since clicking the button named Submit will direct you to the list of Firewall Rules.
Step 6: Check and Apply the Rule
- Now you have created your rule, you can check the list of firewall rules that your system has.
- Edit or delete the rule by clicking the applicable icons next to the rule when it is necessary.
- Once you are satisfied with all settings make sure that the firewall settings have been applied using the Reload Firewall button.
Step 7: Check Active Firewall Rules
- You can see all active rules in the Firewall section. Only very necessary services and ports should remain open on it so that no unnecessary security threats come from it.
- You can update or delete the rules of the firewall as a solution if required by your network security needs.
FAQs
1. What does a Linux firewall do?
A Linux firewall is used to allow or block certain incoming and outgoing network traffic based on predefined rules. It acts as a gatekeeper that filters out unwanted access but allows safe traffic.
2. How do I check if my Linux firewall is running?
To check your iptables, run sudo iptables -L. To check the status of firewalld, use sudo firewall-cmd –state.
3. How can I allow or block specific ports?
Use the -A flag to allow or block ports in iptables and firewalld makes use of firewall-cmd –add-port or –remove-port.
4. Is CyberPanel helpful in managing firewalls?
Yes. CyberPanel offers a page where you can insert, delete, or configure your firewall rules without bringing up the terminal commands.
5. After rebooting, how do I save my firewall rules on my system?
For iptables: Use iptables-save, and for firewalld: ensure that your rules are set as permanent by using the –permanent flag.
Final Take: Harden Your Security Now
Strengthen your servers with powerful Linux Firewall settings and take the security that you have over your network
To sum up, configuring the firewall for Linux is one of the security-related configurations that are made to secure your server from potential threats. Understanding and appropriately managing settings for a Linux firewall allows you to control access to your system, protect your resources, and maintain a safe network.
This becomes granular control over traffic; and with tools such as iptables and firewalld, you can make adjustments here. Even less familiar users can now manage the firewalls in combination with CyberPanel.
Protect your server today with the easy-to-use firewall management tool in CyberPanel. Sign up now and enjoy an atmosphere of safety and control over your Linux system.



