The digital environment is not secure in today’s era. We have to protect our web resources at all times. Cyber-attacks range from subtle to disastrous and have become a continuous challenge for website owners and administrators. Efficient IP address management helps to tackle these threats. You can understand and implement robust IP blocking strategies at a high level of effectiveness in enhancing your website’s security posture.
CyberPanel is a free, powerful, and open web hosting control panel designed with several features that make the management of your website easy and effective. We will talk about why IP address blocking is such an important feature, examine the various options CyberPanel has, and give practical step-by-step instructions on how to block an IP address. We will also discuss best practices, monitoring techniques, and troubleshooting for perfect protection.
Let us get inside how to block an IP address and enhance your website’s security!
Why is It Important to Block an IP Address?
Protecting an IP address is an important consideration in security and the integrity of your website. Here are some of the reasons to block an IP address:
- Preventing unauthorized access: Block an IP address for those looking to hack or other rogue visitors to your site.
- Mitigate DDoS attacks: Block an IP address to block the IPs participating in a distributed denial-of-service attack.
- Reduce spam/malicious activity: Block an IP address to stop spammers or bots from impacting the performance of your site.
- Security Policy Compliance: It is important to block an IP address to ensure sure security of your website. So that it would not be against any specified security protocols and standards.
Methods to Block an IP Address
At CyberPanel, you can have multiple methods to block an IP address. Every method possesses its benefits. Here is one of our top-rated methods.
Blocking IP Address Using CyberPanel Firewall
When you block an IP address, any traffic originating from the blocked IP addresses cannot reach your website. Here is the detail:
Get exclusive access to all things tech-savvy, and be the first to receive
the latest updates directly in your inbox.
- Access the Firewall Interface.
- Open CyberPanel and navigate to Security > Firewall.
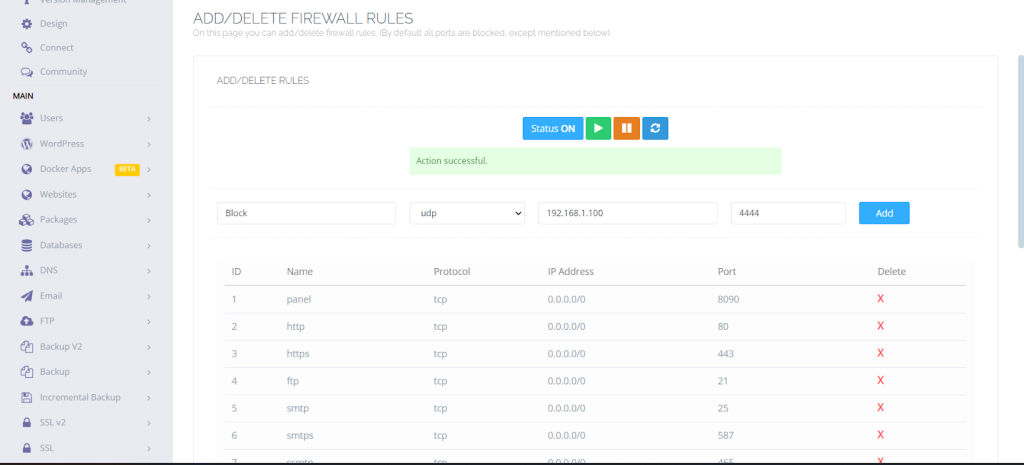
Add New Rule
- Click Add Firewall Rule.
- You have to set the source of the IP address that you want to block.
- Set the Action to Deny.
- Set the Port you can set a specific port or leave it to block all ports.
- Click Submit to apply the rule.
Utilizing .htaccess File to Block an IP Address
You can also use a .htaccess file to block an IP address. Use a file manager to get your website’s root directory.
- Open and create a .htaccess file.
- Add the block rule.
- To do this, add the following code to block one single IP address:
- This will block access from IP 192.168.1.100 to your website.
- Save the .htaccess File.
- Save the file.
Blocking IP Addresses Across Different Platforms
Now we are going to learn how to block an IP address across different platforms.
Blocking IP Address on Linux Servers
- Open the terminal on your Linux server.
- Enter the following command
OR
- Then add the following commands. You have to type your desired IP address & port number in the following commands.
- Now save it
Blocking IP Address on Windows Servers
Here is the method to block an IP address on the Windows server.
Open Control Panel
Go to system and security.
Click on “Advanced Settings”.
Go to inbound rules
Click on ‘New Rule’

Select ‘Custom’ of firewall rule to create
Now, Click on ‘All Programs’
Now select protocols.
Now specify the local and remote IP address to which the rule applies.
Select ‘Block the connection’.
Now specify the profiles.
Now do the following step.
Blocking IP Address on Cloud Services (AWS)
Here are the steps to block an IP address on cloud services.
Go to VPC and find your VPC.
Now locate the primary Network Access Control List associated with the VPC.
Now click on the hyperlink for the NACL ID for the ‘Inbound Rules’ tab.
- Click the ‘Edit Inbound Rules’ button
- On the ‘Edit Inbound Rules’ page. Click the ‘Add new rule’ button.
- Enter a rule number lower than 100 (e.g., 1) to position the new rule before the default ‘All traffic – Allow’ rule.
- From the ‘Type’ drop-down menu, select ‘All Traffic’ to block all traffic from the specified IP address.
- Enter the Port Range you want to block. If you selected ‘All Traffic,’ this step is not necessary.
- Enter the Source IP CIDR range. For a single IP, add /32 at the end.
- Select ‘Deny’ to block requests coming from the IP that matches the specified port range.
- Click on ‘Sort by rule number’ to confirm that the default rule 100 remains at the bottom.
- Save your changes by clicking ‘Save Changes.’
Advanced IP Blocking Techniques
Now, let us know about the advanced techniques to block an IP address:
Geo-Blocking: Blocking IP Addresses Based on Location
Geo-blocking is a process of disabling access to content or services based on a user’s geographic location. It does so by matching the user’s IP address against a geodatabase. Geo-blocking has been used in the past by streaming services, online retailers, and even sometimes governments, in controlling access to content restricted by region.
Advantages of Geo-Blocking:
- Regional Compliance: Makes sure the content is available in the regions where it complies with local laws and regulations.
- Content Delivery by Target: This can ensure region-specific content is delivered to the users, thereby enriching the user experience.
- Security: This can be used to block traffic from regions noted as cyber threat sources.
Disadvantages of Geo-Blocking:
- User Frustration: Users from outside the allowed regions may get frustrated about being blocked from access to certain content.
- VPN Bypass: Geo-blocking can often be bypassed by users using Virtual Private Networks (VPNs), which mask the real location.
IP Blocking Automation with Fail2Ban
Fail2Ban is one of the tools that identify suspicious IP addresses and automatically block them. It scans log files and watches for IPs that exhibit malicious behavior like multiple failed login attempts, then bans them.
What is Fail2Ban?
Fail2Ban is open-source intrusion prevention software that protects servers against brute-force attacks by monitoring system logs for patterns and reacting with temporary or permanent IP blocking.
Benefits:
- Prevents Server Overload: Ensures that no single IP can overwhelm the server.
- Enhances Security: It avoids brute-force attacks and scraping.
- Improves User Experience: Due to the efficient management of traffic, there is a chance of fast and reliable services experienced by legitimate users.
Blocking IP Ranges vs. Single IP Addresses
Blocking an IP range restricts access to a group of IP addresses while blocking a single IP address targets just one address.
Blocking IP Ranges:
This technique is best at blocking whole countries or networks that are known sources of malicious activity.
Example: It can allow the system to block IP addresses originating from a given country or Internet service provider. Blocking of Single IP Addresses:
It is also best for targeting single offenders.
Example: Blocking an IP address that has made several attempts to gain unauthorized access.
Considerations: This could be less accurate since it may block a lot of other legitimate users whereas the latter will be more accurate.
Scalability: The former will be more efficient in case of a large-scale attack.
Monitoring and Managing Blocked IP Addresses
Monitoring blocked IPs implies tracking all the IP addresses that have been restricted and the reasons for such restrictions. Regular monitoring is very instrumental in fine-tuning the list of blocked IPs to ensure that it stays relevant and effective.
Tools for Monitoring:
- Fail2Ban Logs: Tracking IPs that Fail2Ban has blocked.
- Control Panels: Monitor and manage blocked IPs with control panels such as CyberPanel.
Blocked IP List Management and Updates
Of importance is the fact that a block-listed IP list that is regularly updated can maintain the current threats that have been out in the wild. New IPs whose behaviors are reported to be malicious should, therefore, be added, and IP addresses previously blocked but no longer pose a threat should be removed from this blocklist.
Best Practices:
- Period Review: The Blocked IPs List should be periodically reviewed to prevent over-blocking.
- Automated Updates: Automation tools could also update the list of blocked IP addresses in real time based on accumulated data.
IP Monitoring Tools
A few tools exist to monitor IP traffic for potential threats against an organization and make it easier to manage the set of blocked IPs more effectively.
Popular Tools:
- Wireshark: Network protocol analyzer which passively captures and analyzes IP traffic.
- Nagios: Network service monitoring tool that monitors network services, including IP traffic, generating alerts on suspicion of odd activities.
- CyberPanel: This control panel has built-in tools for IP traffic monitoring and setting security variables.
Top Practices for Blocking IP Addresses
To be able to keep up an optimal security posture, you have to observe the following practices:
Regular Updates and Monitoring
- Practice Timely Updates: The firewall and security rules of systems must be updated regularly against new threats.
- Traffic Monitoring: Based on tools provided by CyberPanel, one can monitor remote traffic patterns.
Use of IP Lists
- IP Blacklists: This can be done with the help of third-party IP blacklists to automatically block known malicious IPs.
- Custom Lists: Retain a custom list of IP addresses to block based on the requirement.
Testing and Verification
- Test Rules: After the IP blocks have been set, ensure you test the rules to confirm they are done correctly and work accordingly.
- Check Access: There is to be regular checking to confirm genuine users are not locked out unknowingly.
- Legal and Ethical Considerations
- Avoiding Common Mistakes in IP Blocking
- Regularly Reviewing and Updating Blocked IPs
CyberPanel and IP Address Blocking
CyberPanel is a powerful web hosting control panel integrated with advanced security features on IP address management. It helps you to block an IP address, management of firewalls, and tracking of traffic. Moreover, CyberPanel has a comfortable interface through which anyone can easily block IPs. This platform configures firewalls and automates settings related to security.
Features:
- One-Click IP Blocking: Block IPs from accessing your server in one easy click.
- Automated Security: Configure the rules for the automatic blocking of IPs based on predefined criteria.
- Comprehensive Monitoring: Monitor all of the blocked IPs and manage them easily through an intuitive dashboard.
Advantages of Using CyberPanel in IP Restriction Management
The use of CyberPanel for blocking IP addresses has several advantages including:
- Customization
- Efficiency
- Real-Time Protection
FAQs
What Happens When an IP Address is Blocked?
When an IP address is blocked, no user with that particular IP address will be able to have access to that server or even the website. This might stop some activities of ill-minded users but may also limit some real users who will want proper handling.
Can a Blocked IP Address Be Unblocked?
Yes, an IP address that has been blocked can be unblocked by removing it from the blocklist.
How Do I Know if I Should Block an IP Address?
If an IP address has suspicious activities such as continuous attempts at failed logins, spamming, or unauthorized access then you should block it.
Can IP Blocking Affect My Website’s Performance?
If you properly manage IP blocking then it never affects website performance. However, overblocking or misconfiguration may block access by valid users.
Is IP Blocking the Same as Geo-Blocking?
IP blocking blocks access to particular IP addresses. Geo-blocking disallows access from specific geographic locations. Both techniques can be deployed together in some cases to create greater security.
How Can I Block IP Addresses Automatically?
It can be automated with tools like Fail2Ban and CyberPanel, and the safety features are embedded with predefined rules so that there would be no need for manual action.
Conclusion
In a nutshell, it is important to block an IP address for your website security and an important feature of CyberPanel. With the capability of CyberPanel’s strong firewall, and security module, you are allowed to control traffic effectively and block possible vicious traffic. You must stay updated on this regularly so that your strategy does not remain outdated.



