This is the era of modern enterprises, data is essential for everyone. The volume of data that systems, applications, and networks generate is overwhelming with technological advancement. All this information is usually recorded in the form of logs. These logs rely upon the IT infrastructure’s health, performance, and security. Log management is a practice whereby logs are collected, stored, analyzed, and monitored to bring smooth operations and notice the problems as they occur. Additionally, server log management focuses on the logs that are generated by servers. This helps in improving performance.
It merely paves the way to a systematic process of handling the log data i.e. from its generation to deletion. This encompasses collecting logs from various sources, safe storage, analyzing them for insights into the data, and monitoring the log to trace any inconsistency. Proper log management puts you ahead of potential pitfalls before they become serious and reg-compliant, thus enhancing the security structure at the end of it all.
In this guide, you will get to know everything about log management and server log management. Additionally, you will know how CyberPanel is simplifying tasks for IT infrastructures. Let us get to our technical journey!
Log Management
The process of handling log data in general, from creation to deletion, is called log management. It includes collection, secure storage, and analysis of logs to get insights. Logs should also be monitored to detect abnormalities. It would thus help a system to be able to identify a problem that could be developing in a system way before it happens, to be compliant with various regulations, and to enhance the overall security of the system.
Importance of Log Management
Log management is very crucial for maintaining the health and security of an IT infrastructure. Here are some key points of its importance:
Troubleshooting and Diagnostics
Logs help trace back the cause of system errors, crashes, or poor performance.
Get exclusive access to all things tech-savvy, and be the first to receive
the latest updates directly in your inbox.
Security Monitoring
Regular scanning of logs will make sure that every unauthorized access, malware, or other security risk is captured.
Compliance
A lot of industries demand that log data be kept for purposes of auditing and meeting regulatory standards.
Operational Insights
Logs can provide all manner of useful information regarding the behaviors of a system that can be used in optimizing its performance.
Key Components of Effective Log Management
Here are some key components of effective log management:
Data Collection: Gathering Logs from Multiple Sources
The process of log management starts with the collection of logs from several sources. The data collected have to be aggregated in some central system in which it will get accessed and analyzed.
Log Storage: Best Practices for Storing Logs
The logs will need to be stored after collection with proper security measures. Good storage will see to it that logs will always be availed any time of need for purposes of analysis and audit for compliance. Examples of best storage practices include:
Centralized Storage
A single storage point ensures ease of location of log files for management and analysis.
Secure Storage
Logs must be securely stored at all times to avoid unauthorized access.
Scalability
Make certain of storage solutions that are scalable in size and can serve the increasing volumes of logs in the future.
Server Log Management: A Critical Aspect of Log Management
What are Server Logs?
Server logs are a set of files that contain records of events, transactions, and messages that are being generated by the servers. These log files deliver minute details about server operations, such as access requests, errors, and security-related events.

Types of Server Logs: Access Logs, Error Logs, and More
Server logs have several types. Each type serves a specific purpose. Here is the elaboration
- Access Logs: This type of log records all the access requests to the server.
- Error Logs: This log provides information about any error or problem the server encounters.
- Security Logs: This logs all the security-related events, like unauthenticated logon attempts, changes in user groups, and permission changes.
- Application logs: Following up on performance and other essential aspects of the applications with a server should be possible.
Managing Server Logs
Proper server log management must rely on the best practices that guarantee the accumulating, storing, and analyzing of logs in the following ways:
- Constant Monitoring: Continuous analysis of the server logs should be done in real-time for possible problems.
- Automate Alert Configuration: Automate alert configurations on critical events including multiple failed log-in attempts and uncommon traffic spikes.
- Log Rotation: Create policies for log rotation to avoid log overloads in storage and effectively manage log files.
- Backup Logs: Logs of servers should be backed up periodically to ensure data is not lost and is available when required for auditing.
Common Challenges in Server Log Management
Here are some common challenges:
- Volume of Logs: Sometimes, the amount of log data generated by servers is quite overwhelming and hard to store or analyze effectively.
- Data Correlation: In such large amounts of data, correlating information from different server logs may be a time-consuming process for pattern and trend identification.
- Security Risks: The logs contain sensitive information, so the logs must be securely stored and managed to prevent unauthorized individuals from accessing private information.
Tools and Solutions for Server Log Management
Several tools and solutions are readily available that can facilitate server log management processing. These tools offer real-time monitoring and automated alerts with advanced analytics capabilities to help IT teams, which can be used to resolve the difficulties of server log management.
Role of Log Management in Cybersecurity
Log management is one area where insights obtained on potential threats help companies prepare themselves to respond to incidents.
Cyber Threat Detection and Mitigation Using Logs
Detection and mitigation of cyber threats can be very instrumental by using logs. Security teams can trace suspicious activities, be it unauthorized access malware infection, or data exfiltration. Here are some key aspects:
- Anomaly Detection: It helps in showing the abnormal trends in log data that, when taken as a whole, might point out the possibility of a security breach.
- Incident Response: Attacks are traced back to the point of origin from the logs and action is then taken.
- Forensic Analysis: This follows after an incident to know how it happened to help in future prevention of the same.
Compliance and Regulatory Requirements
Many industries have mandatory regulatory compliances and require log data to be captured and maintained. Log management pays the resulting benefit of ensuring that an organization is in line with the set regulations to prevent potential fines and legal implications. Compliance-related areas include:
- Audit Trails: Development and maintenance of a comprehensive log that can provide an audit trail of all activities.
- Data Retention: The retention of logs for the required period as laid down by the regulations.
- Data Integrity: Log data shall be protected against tampering or unauthorized access.
Incident Response Log Management
Incident response relies heavily upon logs to identify and remediate security incidents. Logs can be instrumental in:
- Determining Source: Identifying the source of the attack or incident.
- Tracking Impact: Following the path of the destruction or compromise.
- Directing Recovery: Identifying what needs to be repaired.
Advanced Log Management Strategies
Log management integration with SIEM systems enhances security by giving an overall view of the IT environment. SIEM systems aggregate logs from many sources, correlate events, and provide advanced analytics to detect and respond to threats.
Modern log management should, as we have seen, involve automation. This way, the human effort required in log collection, storage, and analysis will be significantly reduced. The below activities can be done with automated log management tools:
- Automated Log Collection: Logs are to be collected from different sources without any manual intervention.
- Automated Log Analysis: Machine learning and AI analyze logs and identify anomalies.
- Automate compliance reporting: Automatically generate compliance reports to save a lot of time and effort.
AI and Machine Learning for Log Analysis
- Predict Issues: Use predictive analytics to identify potential issues before they occur.
- Improve Security: Facilitate detection of previously unknown threats with improved security based on log data.
The transformation of log analysis has begun with the advent of artificial intelligence and machine learning, which enable more advanced analyses of the log data.
- Identify Patterns: It can identify patterns and trends buried within log data, which a human log analyst might miss.
Implementation of Log Management
Here are some guidelines by which you can attain efficient log management. Let us start with the steps for setting up a log management system.
Steps to Setup a Log Management System
The following are the steps to be followed to set up a log management system:
- Defining the objectives: It is important to define objectives for log management. For example, is it about security, compliance, or performance optimization?
- Selecting tools: You have to select more appropriate tools for collecting, storing, and then analyzing logs.
- Implementation of Policies: Develop and deploy log retention, archiving, and access policies.
- Monitor and Review: Log data needs to be periodically reviewed.
Scalability in Log Management
When the log data volume increases with time, the need for enhancing the ability of the log management system to scale and load support becomes very crucial. Here are some strategies to manage:
- Choose Scalable Solutions
- Optimize Storage
- Periodic Review and Optimization.
Regular Auditing and Optimization of Log Management Practices
The regular audit and optimization of log management practices are necessary to ensure that the system is effective and efficient in complying with industry standards. Some of the important activities that come under this include:
- Audit
- Optimize Processes
- Update Policies
How CyberPanel Helps You in Log Management
CyberPanel plays an important role in the management of logs. Being a web hosting control panel we possess high-power facilities that will enable effective log management. We provide ease and convenience to server administrators in their effort to maintain a safe and effective IT environment.
How CyberPanel is Used by Businesses to Manage Logs
Many businesses depend on CyberPanel in the case of log management because of its ample features and ease of utilization. Some case studies have pointed out how CyberPanel is successfully being used by an organization to achieve several purposes, such as enhancing security, improving performance, and ensuring compliance.
So, handling logs becomes critical for efficient and effective management, especially as IT environments become complex. CyberPanel log viewer provides valuable insights to users. Here is some description.
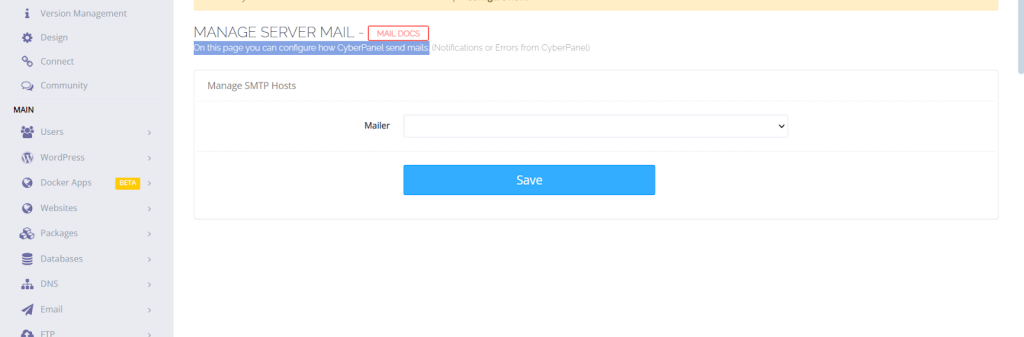
Server mail:
On the server mail page, you can configure how CyberPanel sends mail.
CyberPanel Main Log:
CyberPanel main log corresponds to errors generated by CyberPanel for your domain errors log.
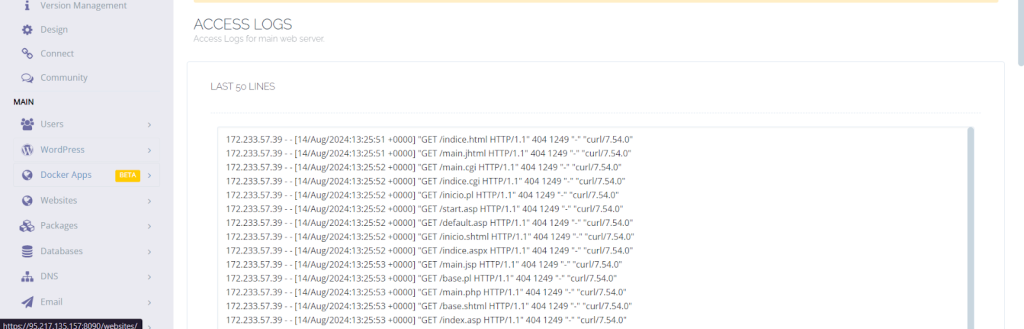
Access Logs:
This page gives you access to logs for the main web server.
Error Logs:
You can have error logs for the main web server on this page.
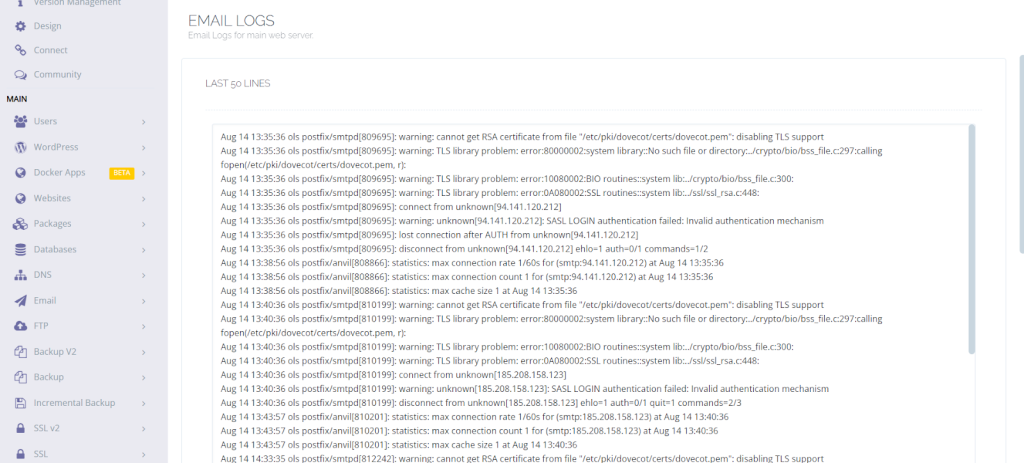
Email Logs:
You can have email logs for the main web server on this page.
FTP Logs:
On this page, you can have FTP logs for the main web server.
ModSecurity Audit Logs:
This page provides detailed logs about any transaction and also gives directions for errors.’
FAQs
1. What are the major components of effective log management?
Effective log management entails data collection, storage, analysis, and monitoring, along with retention. All of these components are related to the goal of having a secure and efficient IT environment.
2. What is the difference between log management and server log management?
Well, it is only specific to the logs coming from servers, which includes those of a web, database, or application nature. It implies a specialized system of tools and best practices to ensure server performance and security are optimized.
3. How does CyberPanel assist in log management?
CyberPanel has very useful built-in log management tools for the collection, analysis, and monitoring of server logs. With CyberPanel, you can manage your server logs efficiently to improve the security and compliance of your server with industry regulations.
Conclusion
Log management and server log management form the most crucial part of IT infrastructure. Log management plays a very key role in system performance, security, and compliance. With the robust functionalities integrated into CyberPanel can highly simplify and enhance your processes of log management to be swift, secure, and compliant in a fast-evolving digital world.