Managing password expiration in Linux is essential for maintaining security and preventing unauthorized access. System administrators must ensure that users change their passwords periodically, in line with security policies. This article covers various methods to check user password expiry date in Linux, how to modify password expiration settings, and how to check SSL/TLS certificate expiry dates.
Understanding Password Expiry in Linux
Linux manages user password expiry date in Linux policies through the shadow file (/etc/shadow). This file stores encrypted passwords and expiry details, including the last password change date, maximum password age, and warning period before expiration.
Each user’s password policy includes:
- Maximum age – Number of days before a password expires.
- Minimum age – Number of days before a user can change their password.
- Warning period – Number of days before expiry when the system starts notifying the user.
- Inactive period – Number of days after expiry before the account is locked.
Now, let’s explore the different methods to check and modify password expiry settings in Linux.
How to Check User Password Expiry Date in Linux
Using the chage Command
The chage command is the most commonly used tool to check password expiration details.
To check the user password expiry date in Linux details for a specific user, run:
Get exclusive access to all things tech-savvy, and be the first to receive
the latest updates directly in your inbox.
chage -l usernameFor example, to check the expiry details of user john, run:
chage -l johnOutput Example
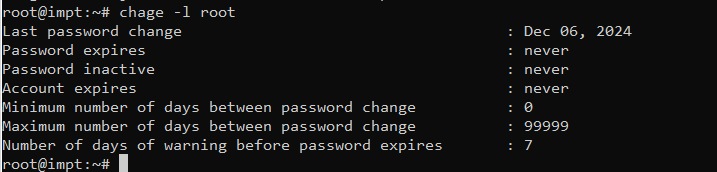
This method provides a clear overview of a user password expiry date in Linux settings.Using passwd -S Command
Another quick way to check password expiry is:
passwd -S usernameFor example:
passwd -S johnOutput Example
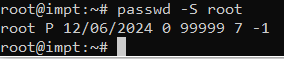
This method is faster but provides less detail compared to chage.
Checking Expiry in /etc/shadow File
The /etc/shadow file stores password expiry details.
sudo cat /etc/shadow | grep usernameFor example:
sudo cat /etc/shadow | grep johnTo decode the last password change date, use:
date -d "1970-01-01 +19345 days"How to Change Password Expiry Date in Linux
System administrators can modify password expiration settings using the chage command.
Set a New Expiry Date
To set a password expiration date, use:
sudo chage -E YYYY-MM-DD usernameFor example, to set john’s password expiry to March 30, 2024:

sudo chage -E 2024-03-30 Change Maximum Days Before Expiry
To change the maximum days a password remains valid, use:
sudo chage -M 60 username
This sets the password expiry to 60 days after the last change.Set Warning Days Before Expiry
To notify users 7 days before expiry:
sudo chage -W 7 usernameThese commands help enforce password policies and ensure timely updates.
How to Check Certificate Expiry Date in Linux
SSL/TLS certificates are crucial for encrypting web traffic and ensuring secure connections. If a certificate expires, users may see security warnings when accessing the website.
Check SSL/TLS Certificate Expiry Using OpenSSL
To check the expiry date of an SSL certificate, use the openssl command:
openssl s_client -connect domain.com:443 -servername domain.com 2>/dev/null | openssl x509 -noout -datesFor example:
openssl s_client -connect example.com:443 -servername example.com 2>/dev/null | openssl x509 -noout -datesOutput Example
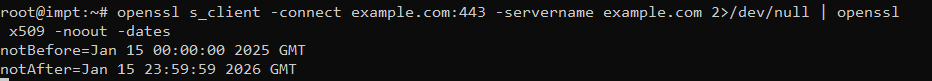
- notBefore – The date when the certificate became valid.
- notAfter – The certificate’s expiration date.
If the certificate is about to expire, renew it to prevent security issues.
Check Local Certificate Expiry
If the certificate file is stored locally, check its expiry date using:
openssl x509 -enddate -noout -in /path/to/certificate.crtFor example:
openssl x509 -enddate -noout -in /etc/ssl/certs/example.crtThis command retrieves the expiration date of the certificate.
Automate SSL Certificate Expiry Monitoring
To automate SSL expiry checks, use a script:
#!/bin/bash
DOMAIN="example.com"
EXPIRY_DATE=$(openssl s_client -connect $DOMAIN:443 -servername $DOMAIN 2>/dev/null | openssl x509 -noout -enddate | cut -d= -f2)
echo "SSL certificate for $DOMAIN expires on: $EXPIRY_DATE"
Schedule this script with a cron job to run daily and alert administrators before expiry.
How to Check Cert Expiry Date in Linux
The term “cert” refers to various digital certificates, including SSL/TLS certificates, SSH keys, and software signing certificates.
For self-signed or CA-issued certificates, use:
openssl x509 -in /path/to/cert.pem -noout -text | grep "Not After"For example:
openssl x509 -in /etc/ssl/certs/server.pem -noout -text | grep "Not After"This displays the expiration date:
Not After : Apr 01 23:59:59 2024 GMTIf your certificate is stored in the Java Keystore (JKS), check expiry with:
keytool -list -v -keystore /path/to/keystore.jks | grep "Valid until"Best Practices for Password & Certificate Expiry Management
To prevent issues related to User Password Expiry Date in Linux or certificate expiry, follow these best practices:
For Passwords:
- Set a reasonable expiry policy to enforce security without disrupting users.
- Use
chage -Wto send early expiry warnings. - Automate expiry checks using cron jobs and scripts.
For SSL Certificates:
- Use Let’s Encrypt for auto-renewing free SSL certificates.
- Schedule monitoring scripts to detect upcoming expiry dates.
- Keep backups of certificate files in case of renewal failures.
Conclusion
Checking password and certificate expiry in Linux is vital for system security. Administrators can use commands like chage, passwd -S, and openssl to check expiry details and update settings as needed. Automating these checks ensures smooth system operations and prevents security risks.
By implementing best practices and monitoring tools, organizations can proactively manage password policies and SSL certificates, reducing downtime and security threats.
FAQs
1. What happens when a user’s password expires in Linux?
When a user’s password expires, they won’t be able to log in until they reset it. If an account expiration date is also set, the account may be locked entirely.
2. What is the difference between password expiry and account expiry in Linux?
Password Expiry – Requires the user to change their password after a certain period but allows them to continue using the account.
Account Expiry – Completely disables the account after a specified date, preventing login until an admin reactivates it.