With the threat changes coming at such high speed, securing your Linux systems today is now very crucial in the digital world. Conversely, many still prefer the open-source operating system due to its flexibility and reliability as well as security features; however, default installation alone might not be enough against possible attacks. As a factor, this is entering the area of hardening Linux, which is an important process of increasing the security of operating systems, based on Linux. This article explores ideas about hardening Linux working systems and will bring you a convenient checklist along with practical knowledge of how to harden your Linux server properly.
Understanding Linux Hardening
This is the process by which vulnerabilities of a Linux server or system are reduced while minimizing its attack surface. Techniques to harden a Linux server include disabling unnecessary services, applying security patches, and strict user permissions. Such practices allow the administrators to increase the security of their Linux environment, and avoid unauthorized access, data breaches, etc.
Importance of Hardening Linux Operating Systems
Reducing the Risk: As Linux is widely used in enterprise environments, cybercriminals are more interested in Linux. Thus, with hardened operating systems, organizations will reduce the risk of making successful attacks.
Compliance: Many industries require a particular level of security standard, and there are regulations (for example, PCI-DSS, HIPAA) that require to be met. Hardening Linux systems can help an organization meet these compliance requirements.
Improved Performance: The redundant services and configurations are disabled so that a hardened system can perform better and conserve resources.
Increased Trust: Their clients and other stakeholders will more than likely trust organizations that give importance to security when it allows them to achieve an edge in the marketplace.
Get exclusive access to all things tech-savvy, and be the first to receive
the latest updates directly in your inbox.
Linux Hardening Checklist
To harden your Linux operating systems properly, here is a comprehensive checklist incorporating every aspect of system security :
1. Linux Hardening: Keep Your System Updated
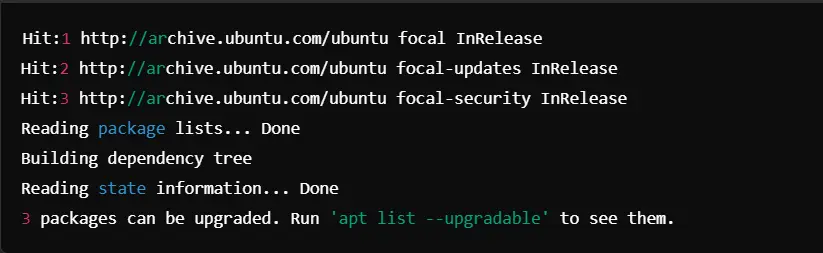
One of the critical steps in hardening the Linux system is keeping the system updated. Keeping the system updated paves the way to fill bugs and increase security.
The command for updating the system:

2. Linux Hardening: Unused Services
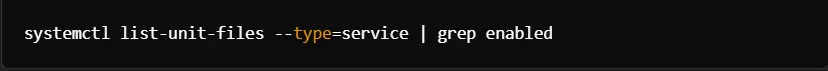
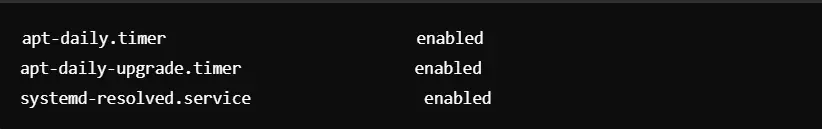
You need not have any services running on your system that are unnecessary. You can turn off the ones that are not required to be in operational functionality within your system.
Command to display the list of active services:
3. Linux Hardening: Safeguard User Accounts
One of the measures to prevent users from getting access to the system is managing user accounts. For this, follow the practices given below:
- Implement Password Policies: Policies can be implemented to enforce complex passwords.
- Limit User Privileges: Give only the required permissions to the users.
- Disable Root Login: The direct root login is a big security risk.
Command to disable root login via SSH:
Edit the SSH configuration file:

Change the following line:

Restart the SSH service:


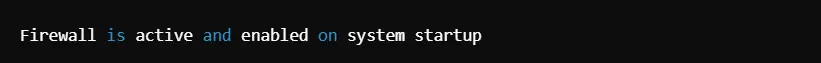
4. Linux Hardening: Implement Firewall Rules
This serves as a wall between your system and outside threats. Configure the firewall to permit only essential traffic only.
Command to install and enable UFW (Uncomplicated Firewall):

Command to allow SSH connections:

5. Linux Hardening: Configure SSH Security
Although probably the most common remote access tool for Linux servers, all variably configurable settings or variables associated with SSH should be secured, even by applying a few of the steps below:
Change the default SSH port: The default on a Linux server is port 22. Changing the default port can reduce automation attacks.
Change SSH Port Command
Edit SSH configuration file:

Change the line:

- Use SSH key authentication: SSH keys provide a more secure method of logging in compared to passwords.
Generate SSH Key:

Copy the key to the remote server:

6. Linux Hardening: Monitor Logs Regularly
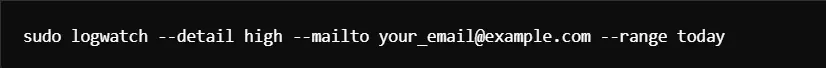
One of the easy ways to identify potential security incidents early is by monitoring system logs regularly. Log analysis might be simplified with tools like logwatch.
Command to install logwatch:

7. Linux Hardening: File Integrity Monitoring
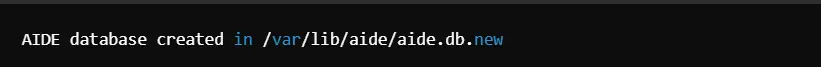
Monitor file integrity. Most system files will be included in this category, indicating whether or not there have been unauthorized changes. Tools to use: AIDE, or Advanced Intrusion Detection Environment.
Command to install AIDE:

Initialize AIDE database:

8. Linux Hardening: Turn Off IPv6 if Not Used
If your organization does not make use of IPv6, you may disable it as it will minimize your attack surface.
Command to turn off IPv6:
Edit the GRUB configuration:

Add the following line:

Update GRUB:

9. Linux Hardening: Back up Your Data Periodically
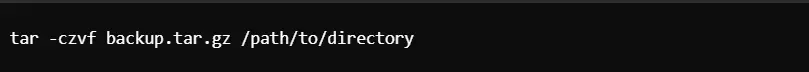
It will help you not to lose data due to any attack or system failure. The necessary tools that can be used for the same are rsync or tar to copy the data backup.
Tar Command for Creating a Data Backup

10. Linux Hardening: Utilize Security Tools and Procedures
Implement more strengthening measures to the security of your Linux system:
Installation of Fail2ban: It is a utility that prevents brute force attacks through the banning of IP addresses that show signs of malevolent activities.
Install command in Fail2ban:


11. Linux Hardening: Monitor Installed Software
One should regularly review the installed packages and remove any unnecessary packages to reduce potential vulnerabilities.

12. Linux Hardening: Harden Network Settings
Secure the network settings to limit illicit access to your system.
Disable IP forwarding if not in use. vim /etc/sysctl.conf

Add the following line:

Reload sysctl settings:

Role of CyberPanel in Linux Hardening
CyberPanel is an advanced web hosting control panel that makes the management of Linux servers easy yet adds to their security. While using CyberPanel, system administrators can implement various techniques for Linux hardening better. Let’s see how the CyberPanel plays a crucial role in Linux hardening:
User Management and Permissions: CyberPanel makes it simple to manage user accounts and permissions. By enforcing strict policies towards the users and minimizing all kinds of unauthorized access rights, you will make your Linux server have less of an attack surface. By this panel, you would be getting a feature of creating and managing the roles of the users, which means only authorized persons will have access to your critical system resources.
Automatic Updates: The best practice for hardening Linux is keeping your system up-to-date. CyberPanel allows you to keep the underlying server updated by automatically applying security patches on time with no manual intervention involved. This helps ensure the attacker cannot exploit vulnerabilities.
Firewall management: CyberPanel manages firewall management and lets you configure and manage rules directly from the control panel. It adds an extra layer of security since it blocks those who attempt to access your server without permission due to proper firewalls.
Manage SSL Certificate in the Domains: You can also easily manage the SSL certificates of your domains with CyberPanel. This will encrypt data exchanged between users and your server. Besides other hardening steps for Linux servers, implementing SSL is an important action that prevents the eavesdropping of sensitive information.
Monitoring and Logging: CyberPanel has in-built monitoring tools whereby the administrator of the setup can monitor the performance status of the servers. In addition, they keep security logs for easier monitoring. By reviewing logs, you can observe unusual or suspicious activity that calls for your attention as an administrator, regarding the security threats.
FAQs: Linux Hardening
1. What is Linux hardening?
Linux hardening refers to securing a Linux system by minimizing vulnerabilities and reducing the attack surface. It involves best practices, such as updating software, managing user permissions, and other configuration in security settings.
2. Why is Linux hardening important?
Linux Hardening and Linux server hardening will help safeguard the site from access attacks, data breaches, and other forms of cyber attacks. Since cyber-attacks are rampant, hardening Linux will improve the chance of organizations protecting their data and sustaining the integrity of their system.
3. Is Linux hardening a one-time activity?
No, to harden Linux server is very much a continuous process. Continuous processes must be carried out in the following areas: updates, monitoring, and audits for security concerns as well as to safeguard the system from newer threats and vulnerabilities.
Conclusion: Secure Your Linux Now!
To sum up, Linux Hardening is very important today to safeguard your systems against further cyber-evolving threats. You can properly utilize tools such as CyberPanel if you follow the best practices for Linux hardening, therefore improving its security and diminishing any possible vulnerabilities.
What’s Next?
Act before a security breach—get on the bandwagon and learn about Linux hardening techniques today. Come and explore CyberPanel’s features and harden your Linux environment!



