Kubernetes has changed the way applications are deployed, scaled, and managed in a containerized ecosystem. Kubernetes offers a solid foundation for automating deployment and container orchestration at scale. The Service object at the center of Kubernetes networking is a key building block that abstracts and exposes applications to the outside world or internally within the cluster.
Among the frequently misconceived concepts of Kubernetes Services, the difference between port, targetPort, and nodePort is perhaps one of the most important. All three are significant, but this article particularly addresses Kubernetes Service Port vs TargetPort: What are the Differences and How do They Work Together Kubernetes Service port vs targetPort, explaining their differences, how they interact with each other, and showing how they behave in real-life scenarios.
Knowledge of these ports’ subtleties is critical to Kubernetes developers, DevOps engineers, and system administrators creating and operating services within a Kubernetes setup. Misconfigure or being unclear on how traffic is communicated between the service and the pods will cause broken applications, unreachability, and possible downtime.
Let us get into the nuances and see the roles of these fields, their interaction with one another, and the best practices in terms of configuring Kubernetes Service Port vs TargetPort in real-world applications.
Kubernetes Services
While comparing Kubernetes Service Port vs TargetPort, Kubernetes Service is an abstraction that establishes a logical group of Pods and a policy for accessing them. As Pods can be ephemeral and can be destroyed or re-created by the scheduler of Kubernetes, Services give clients a consistent endpoint to talk to. Kubernetes Services allow for communication between components within the cluster (for example, from microservice to microservice), and they also allow access to applications from outside the cluster.
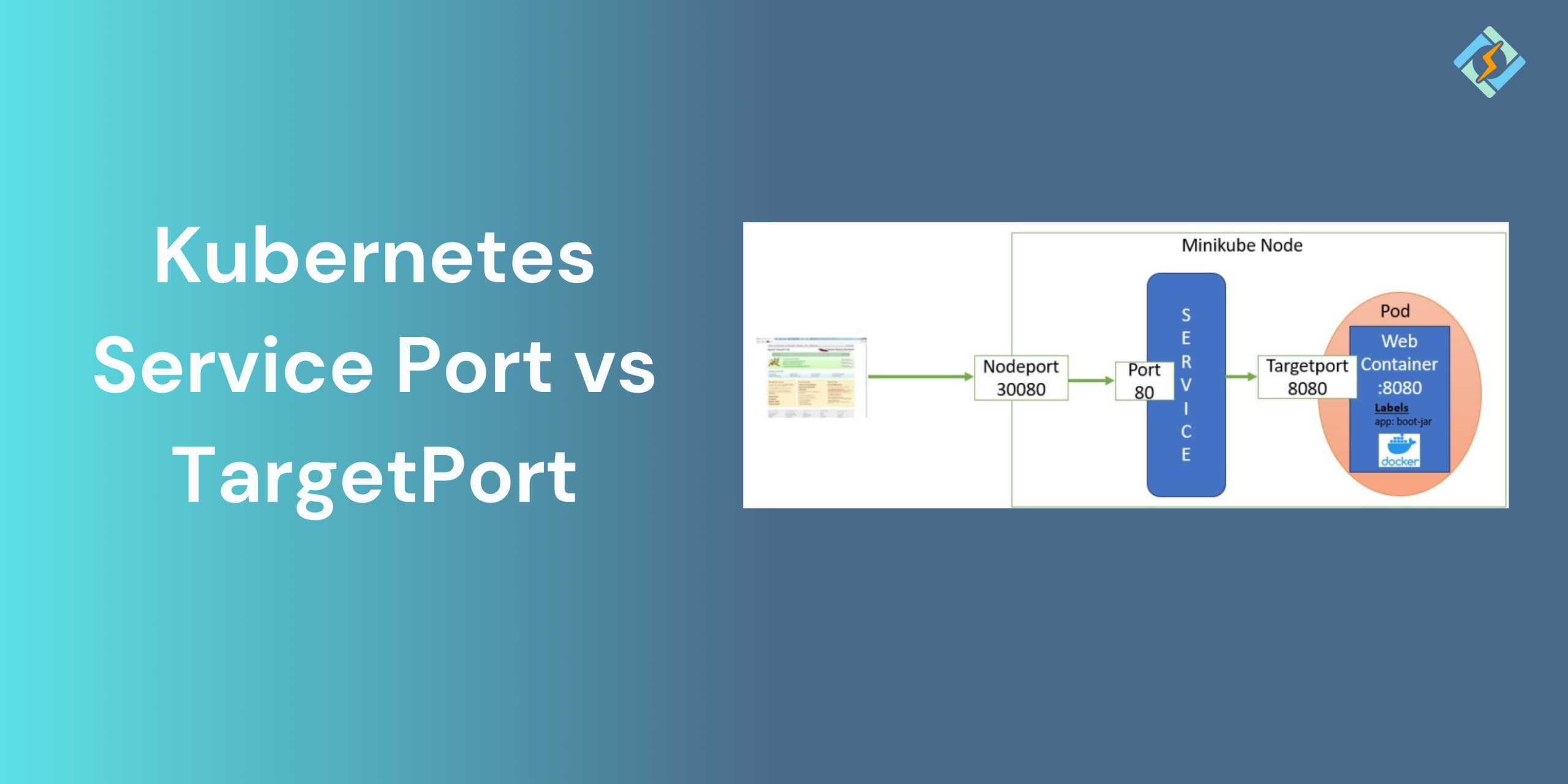
When you establish a service in Kubernetes, you specify multiple ports, such as the port, targetPort, and optionally the nodePort when you are setting up a NodePort service type. These ports specify how traffic is directed from the external world (or another service) to the actual application running within the Pod.
Get exclusive access to all things tech-savvy, and be the first to receive
the latest updates directly in your inbox.
Defining the Key Terms: port, targetPort, and nodePort
Before going into nitty-gritty comparisons, let’s define what each of these terms entails:
- port: This is the port through which the service is exposed. It’s the port that will be used by the clients of the service.
- targetPort: This is the port on the Pod to which traffic will be routed. It is a reference to the port of the container.
- nodePort: This is the port on every Node that can be accessed to use the service outside the cluster (used in NodePort or LoadBalancer service types).
The most frequently mixed-up pair is Kubernetes Service Port vs TargetPort, mainly because both appear to be used for the same purpose. But they operate in a different layer and are utilized in a different context.
Deep Dive into Kubernetes Service Port vs TargetPort
In order to well-understand the difference of Kubernetes Service Port vs TargetPort, imagine Kubernetes Services as a proxy layer between Pods and clients. The Service port is the exposed endpoint on the Service itself, while the targetPort is the internal port on the Pod where the application is indeed listening.
1. port – The Listening Port of the Service
When you specify a Service, the port is where the client will access the application. It is what the service will listen on. If you have a frontend web app that sends requests to a backend service on port 8080, then you would specify that port in the port field of the Service declaration.
This port is the one that is accessible through the Service’s IP address. Any client wanting to access the Service has to go through this port. Internally, Kubernetes will have its own kube-proxy component making use of forwarding from the Service port to the target port of the real backend Pod.
This also implies that port value is attached to the virtual IP (ClusterIP) assigned to the Service, and not the physical ports of the Pods or Nodes.
2. targetPort – The Actual Listening Port of the Pod
The targetPort is the port within the container the one on which your application is executed and listening for traffic. For instance, if your Node.js app is listening on port 3000 within the container, your targetPort is also 3000.
Kubernetes would like to know where to send traffic in the Pod exactly. Therefore, when the request arrives at the Service on the port, Kubernetes is aware to send it to the targetPort for the right Pod.
Notably, what this means is that targetPort is a reference to the actual port an implementation-specific port the containerized application is actually listening on. It may be the same port, or it may be something entirely different.
Mapping Between Kubernetes Service Port vs TargetPort
The port-to-targetPort mapping is the core of the Kubernetes Service abstraction. When you create a Service, you specify a mapping that in effect says:

“When someone sends a request to the Service on port X, route it to the Pod’s port Y.”
This mapping is performed by the kube-proxy and the underlying iptables (or ipvs) rules installed on each Node.
For instance:
<code>apiVersion: v1<br>kind: Service<br>metadata:<br>name: my-service<br>spec:<br>selector:<br>app: myapp<br>ports:<br>- port: 80<br>targetPort: 3000</code>In this case, clients connect to the Service on port 80, and Kubernetes will forward that traffic to the Pods on port 3000.
This comes in handy particularly when the service must expose a standard or known port (such as 80 for HTTP or 443 for HTTPS), but the underlying application may be listening on a different port internally.
Use Cases for Various port and targetPort Values
Probably the most frequent question is: why would you use different values for port and targetPort at all?
The reason is flexibility and abstraction.
Having different values enables:
- Port Abstraction: You can open your application on an ordinary port such as 80 or 443, independent of the internal details of implementation (such as running on port 8080, 3000, or 5000).
- Service Upgrades: You can alter the underlying application to utilize a different port without touching the clients or updating their configurations.
- Multiple Services on One Node: In case your application in containers is making use of non-standard ports, you are still allowed to map them to standard ports on the Service level for client convenience.
For instance, your frontend app may reference my-backend-service:80, but within Kubernetes, the traffic is being forwarded internally to targetPort: 5000.
What Happens When Kubernetes Service port and targetPort Are Equal?
If you do not purposely specify a targetPort, Kubernetes defaults the targetPort to equal the port.
For example:
ports:<br> - port: 8080is functionally the same as:
ports:<br> - port: 8080<br>targetPort: 8080This is a typical case when your service listens on the same port that you desire to expose via the service. It’s neater and easier for small applications or when you have control over both service and the container.
But in the case of production-level systems or when you require clean separation of concerns, it’s advisable to define both fields explicitly.
The Role of Protocol in Services
Kubernetes supports both TCP and UDP protocols for service ports. By default, the protocol is TCP unless specified otherwise.
ports:<br> - port: 80<br>targetPort: 3000<br>protocol: TCPThe protocol field ensures that Kubernetes understands how to handle and route the traffic. If your application uses UDP (e.g., DNS servers), you’ll need to specify it accordingly.
Real-World Example: Service Port Mapping in Action
Suppose you’re running a Django app with Gunicorn that listens on port 8000 locally. But you’d prefer clients to connect through the default HTTP port 80. Your Service definition would be as follows:
apiVersion: v1<br>kind: Service<br>metadata:<br>name: django-service<br>spec:<br>selector:<br>app: django-app<br>ports:<br>- name: http<br>port: 80<br>targetPort: 8000<br>type: ClusterIPHere, the port is 80 (for client access) and the targetPort is 8000 (where the app really listens). Kubernetes automatically forwards the traffic for you.
It enables frontend applications, load balancers, or internal services to use the Django service without needing to know the inner port.
Pitfalls and Troubleshooting
Most developers encounter connectivity problems because of improper port configurations. These are some of the common pitfalls:
- Mismatched Ports: When you specify a targetPort that doesn’t coincide with the actual port the container listens on, traffic will be forwarded but rejected by the container.
- Firewall or NetworkPolicy Restrictions: Even when there are proper port mappings, if Kubernetes Network Policies or other external firewalls are blocking access, you’ll experience timeouts.
- Health Checks Failing: Liveness and readiness probes also need to hit the right port (often the targetPort) in order to accurately determine the status of the application.
- Container Not Listening: Always verify with kubectl exec that the container is actually listening on the defined targetPort.
Best Practices
- Always define both port and targetPort explicitly for clarity and maintainability.
- Use descriptive port names (name: http, name: metrics) when dealing with multiple ports to avoid confusion.
- Ensure that container ports are exposed in your deployment manifest as well.
- Avoid using arbitrary high ports unless necessary; stick to conventions whenever possible.
- Leave your Service port exposed (e.g., 80, 443) as a plain standard for user-facing apps for more compatibility with clients, DNS, ingress controllers, etc.
Advanced Use Case: Multiple Ports in One Service
Kubernetes Services support exposing multiple ports. For instance, if your app exposes http on port 80 and metrics on port 9090, you can describe them like this:
ports:<br> - name: http<br>port: 80<br>targetPort: 8080<br> - name: metrics<br>port: 9090<br>targetPort: 9090Every port can be mapped separately, and clients can connect to either depending on what they want to use.
Conclusion
It is very important to understand the difference between Kubernetes Service port vs targetPort when one is dealing with Kubernetes networking. Although the two fields may appear identical at first look, they are at different levels of abstraction and perform different roles. The port is the one that the Service publishes to the clients, while the targetPort instructs Kubernetes where within the Pod to forward the traffic.
Whether you’re creating microservices, deploying monolithic apps, or configuring intricate CI/CD pipelines, realizing and utilizing port and targetPort correctly makes your services accessible, dependable, and properly configured. Take the initiative to clearly define your ports, grasp your container’s networking, and utilize Kubernetes’ robust abstraction model in order to create dependable and scalable applications
FAQs
Can the Kubernetes Service port vs targetPort be the same?
Yes, and in most cases they are. But declaring them even when equal is good for readability and future changes.
Should I also expose container ports in the Deployment?
Yes. Though Kubernetes does not expect you to declare container ports in the Deployment, it is a good practice to specify them in the container.ports section for better clarity and for utilization of other tools such as probes and debugging.
What if my container listens on several ports?
You may have one Service with more than one ports definitions or individual Services based on architecture and exposure requirements.